Today, we all use the internet for work, to learn new things, and to talk to our friends. But, when we use the internet, there are dangers that can hurt our computers or steal our information. These dangers are called major client side security threats.
In 2025, these threats are very smart and can trick many people. We need to know about these dangers so we can keep our computers and information safe. Today, we will talk about the 12 major client side security threats and how we can protect ourselves from them. Let us start learning about how to keep our internet time safe!
What Are Client Side Security Threats?
Major client side security threats are problems that happen when bad people try to attack the part of your computer or phone that you use to look at websites or use apps. These are the areas where you put in information like your names, passwords, and other details. When you interact with the internet directly, that is where these threats come in.

Think of your device like your house. If someone wanted to sneak in, they might try the windows, doors, or even the mailbox. In the world of computers and phones, major client side security threats are like these sneaky ways that hackers try to get into your device. They might trick you into opening a bad email, clicking on a harmful link, or downloading something that looks fun but is actually dangerous.
By understanding these threats, you can learn how to lock the doors and windows of your device better. This way, you can keep your personal information safe from hackers who want to steal it. So, it is very important to know about these major client side security threats and how to stop them from affecting you and your family.
The 12 Major Client Side Security Threats in 2025
It is important to understand these threats because they target the part of your computer system that you interact with directly, like your web browser and applications. By learning about these issues, you can be better prepared to stop hackers before they can do any damage. So, let us discuss what these major client side security threats are and how you can defend against them to keep your digital life safe and secure.
Threat 1: Cross-Site Scripting (XSS)
One of the big dangers on the internet is called Cross-Site Scripting, or XSS for short. XSS is a kind of attack where bad people put harmful scripts into websites that we trust. Imagine you are writing on a wall where everyone can write. Someone could write something bad that makes your pen stop working or messes up your drawing. That is a bit like how XSS works on websites.
When you visit a website hit by XSS, these harmful scripts run on your computer without you knowing. This can lead to bad people stealing your personal information, like your passwords or even your messages. It is scary because you can not easily see it happening. Here are some simple steps we can take to protect ourselves from XSS:
- Be Careful Where You Click: Just like you would not pick up a candy from the ground and eat it, do not click on links from people or places you do not trust. Sometimes, these links can have hidden scripts that cause XSS attacks.
- Use Trusted Extensions: Some browser extensions can help keep you safe. They check the websites you visit and make sure there is nothing suspicious. It is like having a guard who checks if the wall you are writing on is safe.
- Keep Your Browser Updated: Make sure the internet browser you use (like Chrome, Firefox, or Edge) is always updated. When a browser is up-to-date, it has the latest protection against many types of attacks, including XSS.
- Watch Out for Warnings: Sometimes, your browser will warn you if a website looks dangerous. Always pay attention to these warnings. It is like a stop sign on the road telling you to be careful.
Threat 2: SQL Injection
SQL injection is another serious major client side security threats. It happens when bad people use web forms or URLs to send bad code to a website’s database. Think of it like slipping a fake ticket into a movie theater that tricks the ticket checker into letting more people in for free.
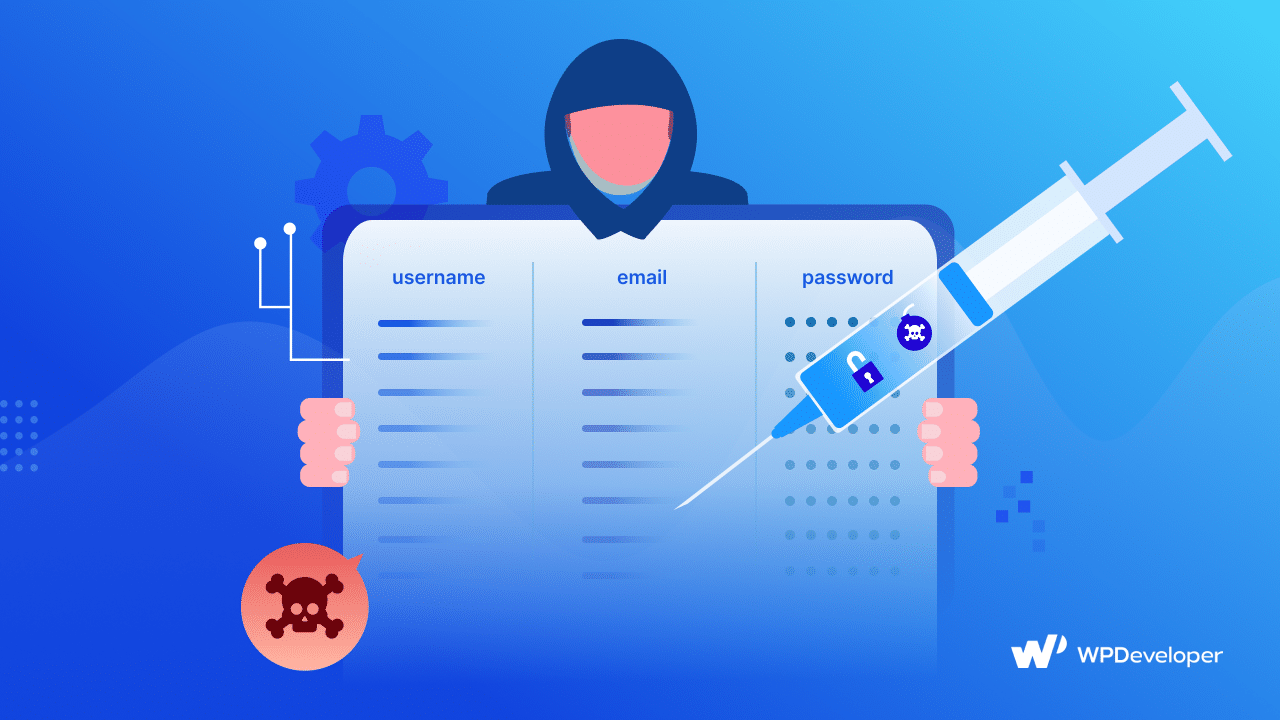
Databases hold all the important information, like user details and passwords. When someone does an SQL injection, they can trick the database into showing or changing information that they should not see or touch. This can lead to big problems, like stealing private information or messing up the website. Here are some ways to protect ourselves from SQL injection:
- Be Careful with Your Information: Be thoughtful about where and how you enter your personal information online. Only fill out forms on websites you trust, and never give more information than you need to.
- Use Strong Passwords: Using strong and unique passwords for different sites is like having a good lock on your door. It makes it harder for hackers to guess and use your passwords to attack databases.
- Keep Software Updated: Just like with defending against XSS, keeping your software updated helps protect against SQL injection. Updates often fix security holes that hackers use to perform these attacks.
- Learn to Recognize Phishing Attempts: Often, SQL injection attacks start with a phishing attempt, where you receive a fake email asking for your information. Knowing how to spot these fake emails can stop SQL injection attacks before they start.
Threat 3: CSRF (Cross-Site Request Forgery)
Cross-Site Request Forgery, often called CSRF, is another major client side security threat that we need to be careful about. CSRF tricks you into doing things you did not mean to do on a website where you are logged in. If someone secretly changed your TV channel using another remote while you thought you were using yours.
CSRF can happen when you click on a bad link or visit a harmful website while you are logged into another site, like your email or bank account. This bad site can send a request, like changing your password, without you knowing. This is dangerous because it can let bad people take over your accounts or steal your personal info. Here is how you can protect yourself from CSRF:
- Log Out of Websites: Always log out from websites when you are done, especially ones where you have important information like your bank or email. It is like locking your car after you park it.
- Be Careful with Links: Just like with other threats, be very careful about clicking on links, especially in emails from people you do not know. If a link looks weird or you did not expect it, do not click on it.
- Use Security Features: Some websites have features that help protect against CSRF. This might include things like “same-site cookies” which make sure requests come from the same website, not a bad one. Always turn on extra security features when you can.
- Update Your Browser: Keep your internet browser updated. New updates often have better security that helps protect against threats like CSRF.
Threat 4: Session Hijacking
Session hijacking is another major client side security threat that we should all know about. This happens when a bad person takes over your online session with a website. For example, if you were playing a video game online and someone else took your controller and started playing as you. That is kind of what happens during session hijacking.

When you log in to a website, a session is started between your computer and the website. It is like a secret handshake that keeps you connected. If someone steals that handshake, they can pretend to be you. They might see your private information, buy things with your money, or change your account details. Here is how you can fight against session hijacking:
- Use HTTPS: Always make sure the websites you use have HTTPS in the URL, not just HTTP. HTTPS is more secure because it encrypts, or scrambles, your information so others can not easily see it. It is like sending a letter in a locked box instead of a clear envelope.
- Log Out after Use: Always log out from websites when you are finished, especially if you are using a public computer or Wi-Fi. This closes your session safely.
- Be Wary of Public Wi-Fi: Public Wi-Fi can be risky because it is easier for hackers to intercept the data you send and receive. If you must use public Wi-Fi, avoid logging into important accounts or use a VPN (Virtual Private Network) which makes your connection more secure.
- Keep Your Software Updated: This includes your web browser and any security software you have. Updates often include fixes for security problems that could allow session hijacking.
Threat 5: Insecure Direct Object References
Insecure Direct Object References, often abbreviated as IDOR, is a major client side security threat that can allow bad people to see or change information they should not have access to. if you could see someone else’s report card by just changing a number on a website. That is what happens with IDOR.
This threat occurs when a website uses simple references to access objects directly, like database entries or files. If these references are not protected well, someone could change them to access other users’ data, like personal details or files. Here is how we can protect ourselves from IDOR:
- Be Careful with Your Information: Always think twice before you enter personal information on a website. Make sure the website is trustworthy and has good security measures in place.
- Check URL Changes: Sometimes, just looking at the URL in your web browser can tell you if the website is using simple object references. Be cautious if you see a number or a name in the URL that looks like it controls what you see on the page.
- Use Websites with Good Security Practices: Websites that have strong security measures are less likely to be vulnerable to IDOR. These websites use methods that hide the direct references or check that you are allowed to see what you are asking for.
- Keep Your Browser Updated: Again, having the latest updates for your web browser can help protect you from many major client side security threats, including IDOR. Browser updates often include new security tools that make it harder for hackers to exploit vulnerabilities.
Threat 6: Security Misconfiguration
Security Misconfiguration is a major client side security threat that happens when websites or online services are not set up correctly. For instance, if someone forgot to close a window in their house before leaving. If a thief walks by, it would be easy for them to get in. This is similar to what happens when an online service is not configured properly hackers find it easier to sneak in.
This threat can occur in many ways, such as when default passwords are not changed, unnecessary services are left running, or when software is not set up securely. Each of these issues can create openings that bad people can use to access private information or disrupt services. Here is how to protect against security misconfiguration:
- Update and Patch: Always keep your software up-to-date. Updates fix security holes that hackers might use to get into your systems.
- Secure Settings: When setting up new devices or software, change default settings, passwords, and usernames to something secure. This includes turning off or removing any software features you do not need.
- Regular Security Reviews: Regularly check your security settings to make sure everything is as tight as it should be. This is like making sure all the windows and doors in your house are locked before you leave.
- Educate Yourself: Learn about the best security practices for the software and devices you use. The more you know, the better you can protect yourself from hackers.
Threat 7: Sensitive Data Exposure
Sensitive Data Exposure is a major client side security threat where our personal and important data can be stolen or seen by others who should not have access to it. Think of it like leaving your diary open on a park bench where anyone walking by could read it.
This kind of exposure can happen when websites do not protect our data well enough. It could be anything from your passwords and credit card numbers to your home address and phone number. If bad people get this information, they can steal from you or pretend to be you. Here is how to protect yourself from sensitive data exposure:
- Use Strong Passwords: Make sure you use strong and different passwords for your online accounts. A strong password is like a strong lock on your diary. It makes it harder for someone to open it and read your secrets.
- Look for HTTPS: Always check that the website you are using has HTTPS in its URL. This means the site is more secure. It is like making sure your diary has a lock before you write in it.
- Be Careful What You Share: Think carefully about the information you put online. Ask yourself if you really need to give this information. It is like thinking twice before you write something really personal in your diary.
- Use Security Settings: Many websites and apps have settings that help protect your privacy. Make sure you understand these settings and use them to keep your information safe. It is like covering your diary with something so people can not easily see it.
Threat 8: Missing Function Level Access Control
Missing Function Level Access Control is a major client side security threat that happens when websites do not properly check if someone has the right to do something, like viewing private files or changing settings. Imagine if anyone at your school could go into the office and look at any student’s records just because the door was unlocked. That is similar to what happens with this threat.
This threat means that once someone is logged into a system, they might access things they should not be able to, just because the website does not check their permissions carefully each time. This can lead to unauthorized changes or exposure of sensitive information. Here is how we can protect ourselves from missing function level access control:
- Be Cautious About Where You Log In: Only log into accounts from your own devices and from secure locations. This makes it less likely that someone else will be able to access your logged-in session.
- Use Websites with Good Security Practices: Choose to use services and websites that are known for their strong security. These websites are better at managing who can see what, making sure only the right people get access to sensitive actions.
- Keep an Eye on Your Account Activities: Regularly check the logs of your online accounts, if available. This means looking at what has been done with your account to see if there is anything you did not do.
- Educate Yourself About Security Features: Understanding the security features and settings available on the platforms you use can help you better protect your accounts. This is like knowing all the exits and doors in your house so you can make sure they are all locked.
Threat 9: Using Components with Known Vulnerabilities
Using Components with Known Vulnerabilities is a major client side security threat that happens when websites use old or unsafe software that has problems that bad people know about. It is like using an old lock on your door that everyone knows can be easily picked.
When websites or apps use these old parts (or components), it gives hackers a chance to break in because they already know what weaknesses these parts have. They can steal information, mess up the website, or even take over the website completely. Here is how you can protect yourself from this threat:
- Update Your Software: Always make sure the software on your devices is up-to-date. Updates often fix old problems that could let hackers in. It is like changing an old lock for a new, stronger one.
- Use Reliable Software: When you choose software, pick ones that are well-known for being safe and get regular updates. It is like choosing a lock for your door that is made by a trusted brand.
- Stay Informed: Keep an eye on news about software you use. If you hear about a problem, look for updates or a way to fix it. This is like knowing that a certain type of lock has been recalled for safety issues.
- Secure Configuration: Make sure your software is set up safely. Sometimes, the way software is set up can leave it open to attacks. It is like making sure your door’s lock is not just installed, but also properly working.
Threat 10: Unvalidated Redirects and Forwards
Unvalidated Redirects and Forwards a major client side security threat where websites send you to other websites without checking if those destinations are safe. Think of it like being told to take a shortcut by someone you do not know, without knowing where it really goes. This can be risky because it might lead you to a dangerous place.
When websites do not properly check where they are sending you, hackers can trick the site into sending you to a bad website. This bad site might look real but can be set up to steal your information, like passwords or even install harmful software on your device. Here is how to protect yourself from unvalidated redirects and forwards:
- Stay Alert to URL Changes: Watch the web address bar in your browser. If you click on a link and the URL changes weirdly, be cautious. It is like keeping an eye on road signs to make sure you are still on the right path.
- Avoid Clicking Suspicious Links: Be careful with links in emails, messages, or websites, especially if they look strange or come from someone you do not know. It is like ignoring advice from a stranger who seems shady.
- Use Trusted Websites: Stick to well-known and trusted websites, especially when you need to enter personal information. Trusted sites are more likely to have the right security to prevent these threats.
- Keep Software Updated: Ensuring your browser and any security software are up to date can help protect against threats that exploit unvalidated redirects and forwards.
Threat 11: Clickjacking
Clickjacking is a sneaky major client side security threat where bad people trick you into clicking on something you did not mean to. Imagine if someone covered a real button with a fake button that looks just like it. You think you are clicking the real button, but actually, you press the fake one.
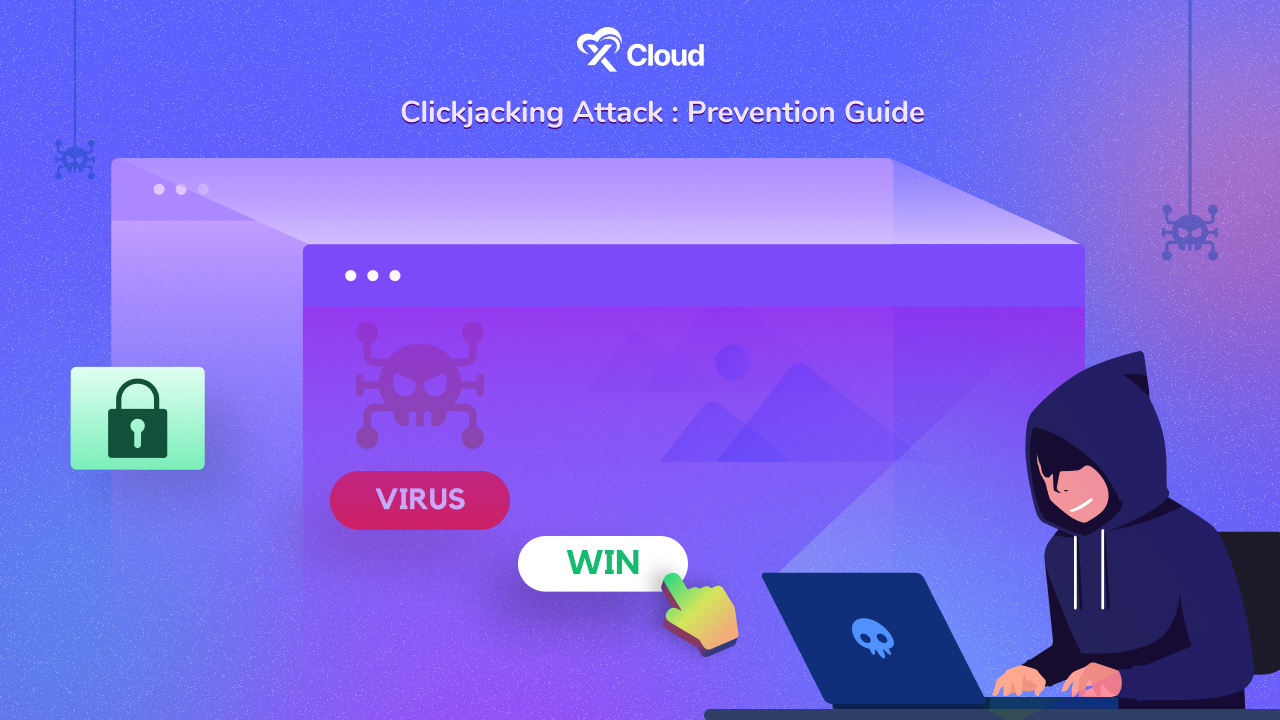
Clickjacking can happen when hackers hide invisible layers over what looks like normal web pages. You might think you are clicking on a video play button, but you are actually giving access to your webcam or liking a page on social media without knowing it.
Here is how you can defend against clickjacking:
- Use Modern Browsers: Make sure you are using a modern and updated web browser. New browsers have better protection against many types of attacks, including clickjacking. They can block those invisible layers.
- Enable Browser Security Features: Many browsers have features that stop bad pages from doing sneaky things. For example, frame busting is a feature that stops other sites from putting hidden frames on the page you are viewing.
- Be Cautious with Links and Buttons: Be careful where you click, especially on websites you do not visit often. If something seems off, like a button not doing what it should, it is better to close the page.
- Use Security Software: Some security programs can help protect against clickjacking by warning you about suspicious websites or blocking harmful content.
Threat 12: Using Outdated or Unsupported Software
Using Outdated or Unsupported Software is a significant major client side security threat. This happens when you keep using old versions of software or apps that no longer get security updates from the creators. Imagine driving a car that has not been serviced for years; it is more likely to break down and is not as safe.
When software is outdated, it may have weaknesses that hackers know about and can easily attack. These attacks can lead to them stealing your private information, taking over your computer, or using it to attack others. Here is how to protect yourself from using outdated or unsupported software:
- Regular Updates: Always update your software and apps whenever a new version is available. These updates often fix security problems that could let hackers in. It is like getting your car regularly checked and serviced to make sure it stays safe.
- Uninstall Unused Software: If you have old programs on your computer that you do not use anymore, it is best to uninstall them. This reduces the chances of bad people finding and using old software to get into your computer.
- Use Supported Software: Make sure the software you use is still supported by the people who made it. Unsupported software does not get updates, which makes it risky. It is like using equipment that no one fixes anymore.
- Security Software: Have good security software installed. This can help protect you by blocking attacks and warning you about risky software on your computer.
Use of Security Tools and Best Practices
Using the right tools and following best practices can greatly help in defending against major client side security threats. These tools and strategies ensure that your online activities remain safe and your personal information is well-protected. Here are some essential security tools and best practices to consider:
- Antivirus And Anti-Malware Software: These are the first line of defense against many threats. They scan your computer for known viruses and malware, and help remove any threats found. Make sure to keep this software updated to protect against the latest threats.
- Firewalls: A firewall helps protect your network by blocking unauthorized access while permitting outward communication. It can be software-based or hardware-based and is crucial for preventing unauthorized access to your network.
- VPN (Virtual Private Network): A VPN encrypts your internet connection, making it secure and private. This is especially important when you are using public Wi-Fi networks, as it helps protect your data from major client side security threats like Man-in-the-Middle attacks.
- Browser Security Settings: Increase your browser’s security by adjusting settings to block unauthorized downloads, disable unwanted plugins, and control site permissions. Regularly clear your cookies and cache to remove personal data stored by websites.
- Strong Passwords And Password Managers: Use complex passwords that are hard to guess. A password manager can help you generate and store these passwords securely. Never reuse passwords across different sites.
- Two-Factor Authentication (2FA): Always enable 2FA where possible. This adds an additional layer of security by requiring not only your password but also a second factor, like a code sent to your phone, to access your accounts.
- Regular Updates: Keep all software, including your operating system, browser, and any installed applications, up to date. Developers regularly release updates to fix security vulnerabilities that could be exploited by attackers.
- Educate Yourself And Others: Stay informed about the latest security threats and how to protect against them. Educate your family, friends, and colleagues about safe online practices to help them avoid common pitfalls.
By integrating these security tools and best practices into your daily online activities, you can enhance your defenses against major client side security threats. Maintaining a proactive approach to cybersecurity can significantly reduce the risk of falling victim to cyber attacks.
Fight Against Client Side Security Threats & Keep Your Online Platform Safe
We have learned about the 12 major client side security threats that are especially important in 2025. By understanding these threats, we can take better steps to protect ourselves online. It involves being aware of the dangers, using the right tools to protect yourself, and always staying alert. We can fight off these major client side security threats and keep our digital space secure.
If you have found this blog helpful, feel free to subscribe to our blogs for valuable tutorials, guides, knowledge, and tips on web hosting and server management. You can also join our Facebook community to share insights and engage in discussions.