Hosting security is a big concern for businesses of all sizes. As websites handle more and more sensitive data, cyberattacks are becoming both more common and more sophisticated. If you run a website, you have to protect it against threats like malware, bot traffic, and even distributed denial of service (DDoS) attacks.
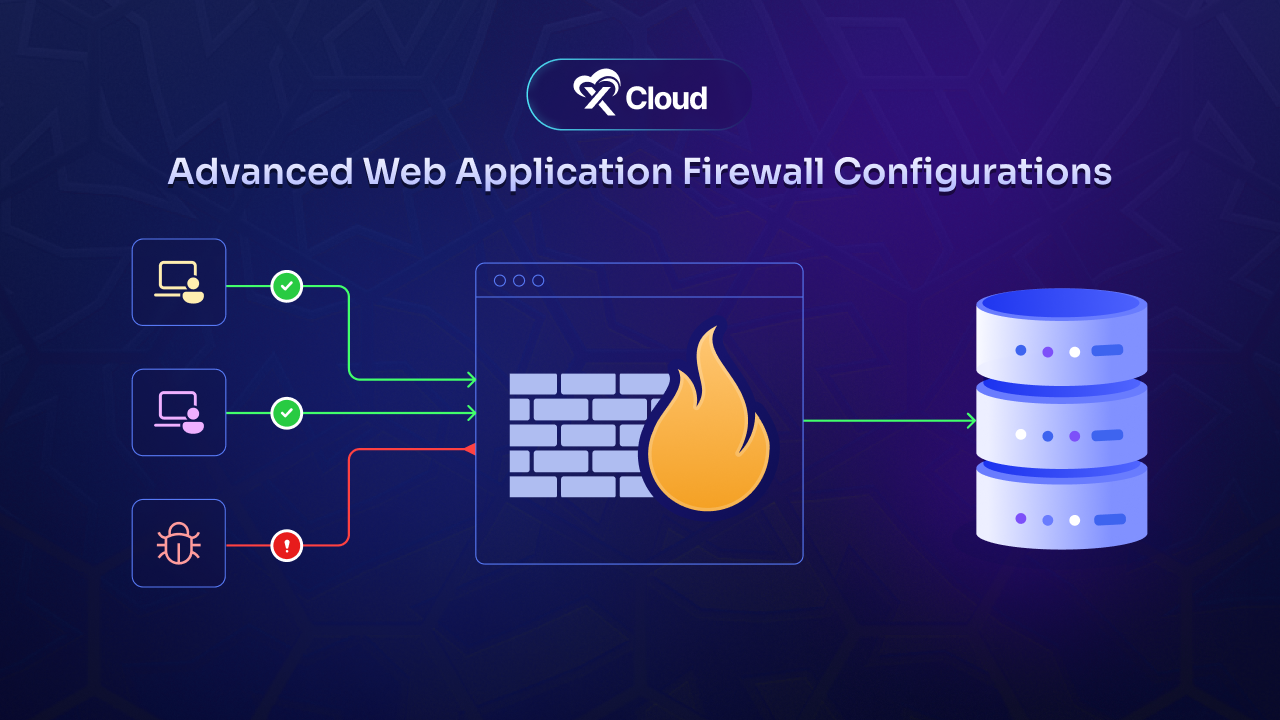
A web application firewall (WAF) can provide strong protection. But with today’s growing threats, a basic WAF setup might not be enough. Today, we will explore how advanced WAF configurations can keep your hosting secure, how they work, and how to implement them.
What Is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security device designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the internet. Unlike traditional firewalls that guard against unauthorized access to the network, WAFs are application-specific. They focus on filtering traffic that directly interacts with the web application. There are three primary types of WAFs:
- Network-based WAF – This type of WAF is installed on-premises and operates at the network level.
- Host-based WAF – Installed directly on the web server, this WAF offers deep customization but can consume resources.
- Cloud-based WAF – Offered as a service, cloud WAFs are easy to implement and scalable.
While traditional WAFs can block common attacks like SQL injection and cross-site scripting (XSS), they fall short when faced with complex, evolving threats. This is where the Advanced Web Application Firewall comes in, offering stronger protection with customizable rules and real-time threat intelligence.
Why Advanced WAF Configurations Are Crucial for Hosting Security?
With the rise of automated bots, DDoS attacks, and highly targeted application-layer threats, having an advanced WAF configuration gives you the edge in identifying and stopping these threats. An advanced web application firewall doesn’t just block attacks based on static rules; it continuously learns and adapts to new attack patterns, using real-time data. Here’s why advanced configurations are essential:
- Adaptability: The modern threat environment is unpredictable and constantly evolving. Hackers constantly find new ways to bypass security defenses. An advanced web application firewall can adapt by updating its rules in real time, unlike a traditional WAF, which relies on static configurations.
- Customization: Every website is unique. While a basic WAF might offer blanket protection, advanced configurations allow you to customize security settings to suit your specific environment, focusing on the risks that are most relevant to your site.
- Layer 7 Protection: Most attacks, like SQL injections or cross-site scripting (XSS), target the application layer. Basic security tools may miss these sophisticated attacks, but an advanced web application firewall focuses heavily on application-level security, ensuring thorough protection.
In today’s environment, where even small websites are targets for automated bots and hackers, having an advanced WAF configuration is no longer optional. It’s an essential part of your security strategy.
Key Features of Advanced WAF Configurations for Hosting Security
Now that we understand why advanced configurations are necessary let us dive into some specific settings that can greatly enhance your Advanced Web Application Firewall. These configurations will not only protect your web application but also ensure that your hosting environment stays secure and resilient against attacks.
1. Traffic Monitoring And Filtering
One of the most powerful features of an Advanced Web Application Firewall is its ability to monitor and filter web traffic in real-time. With advanced monitoring, you can analyze traffic patterns and spot unusual activity that could indicate an attack. For example, you can set up rules to block traffic from certain countries or limit the number of requests from a single IP address. This helps protect against brute force attacks and Distributed Denial of Service (DDoS) attempts.
Advanced traffic filtering allows you to create custom rules. You can filter traffic based on headers, cookies, user agents, or even the content of HTTP requests. By customizing these rules, you can block specific attack vectors while allowing legitimate traffic through. This precision is critical in stopping sophisticated attacks without disrupting regular users.
2. Rule Customization Based on Application Type
Not all web applications are the same, and neither are their security needs. A blog, for instance, will have different vulnerabilities compared to an e-commerce store. With advanced rule customization, you can configure your WAF settings to fit the unique behavior of your application.
For example, e-commerce sites might need stricter security around credit card transactions, while a news site might focus more on protecting its comment sections from spam and cross-site scripting (XSS) attacks. Advanced WAF settings allow you to create specific security profiles for different parts of your web application, ensuring comprehensive coverage.
3. Virtual Patching
One of the most innovative features of an Advanced Web Application Firewall is virtual patching. In the world of web security, new vulnerabilities are constantly being discovered. But applying patches to fix these vulnerabilities can take time, especially if you are working with complex systems or have limited development resources.
Virtual patching is a lifesaver in these situations. With this feature, your WAF can temporarily block attacks targeting a known vulnerability, giving you time to roll out a proper fix. It acts as a temporary bandage, protecting your application from being exploited while you address the issue behind the scenes.
4. Bot Management And Rate Limiting
Bots can be both useful and harmful. Some bots index your site for search engines, while others try to exploit your site by scraping data or launching automated attacks. With advanced WAF configurations, you can differentiate between good bots and malicious ones.
Bot management tools can block harmful bots or limit their activity, preventing them from overwhelming your servers or scraping sensitive information. Rate limiting is another key tool here. This allows you to control how many requests an IP address can make in a certain time period, which helps in mitigating DDoS attacks and reducing server strain.
5. Application Layer Protection (Layer 7)
When it comes to security, the application layer (Layer 7 of the OSI model) is often the most vulnerable. Most web application attacks, such as SQL injection or cross-site scripting (XSS), happen at this level. A basic firewall might not be able to detect these threats, but an Advanced Web Application Firewall provides specific protections for Layer 7.
With Application Layer Protection, your WAF will inspect the actual content of web requests to detect malicious patterns. For instance, if someone tries to insert malicious SQL queries into your site’s forms, the WAF can block the request before it reaches your database. This layer of protection is essential for preventing some of the most dangerous web attacks.
Core Configurations for Advanced Web Application Firewall
To get the most out of an Advanced Web Application Firewall (WAF), you need to focus on key configurations. These configurations determine how your firewall will react to potential threats and protect your hosting environment from cyber-attacks. Here, we will break down some of the most important settings that every advanced WAF should have.
1. Firewall Policies
Policies are the backbone of any firewall system. In an Advanced WAF, firewall policies are used to define which traffic is allowed and which should be blocked.
- Default Deny Policies: This means that unless the traffic explicitly meets specific criteria, it will be blocked. This type of policy is crucial in a hosting environment where the risk of malicious traffic is high.
- Allow Lists (Whitelisting): Trusted IP addresses, users, or applications can be added to the allow list, granting them access while blocking others.
- Deny Lists (Blacklisting): This involves identifying known malicious IP addresses or countries from which attacks typically originate and preventing any traffic from these sources.
2. IP Blacklisting And Whitelisting
IP blacklisting is one of the most straightforward ways to block malicious traffic. In an Advanced WAF, this feature is typically more robust, allowing you to create dynamic blacklists that automatically update based on real-time threat intelligence.
- Geofencing: You can block or allow traffic from specific geographical locations based on your business needs.
- Whitelisting Internal IPs: This is essential for ensuring that your own employees or trusted partners can access your web applications without being accidentally blocked.
3. Rate Limiting And Traffic Shaping
Rate limiting controls how many requests a user can make to your web application in a given time. Without rate limiting, an attacker could bombard your server with thousands of requests per second, causing it to slow down or crash.
- Set Thresholds for Requests: You can configure your Advanced WAF to only allow a certain number of requests per IP address within a specific timeframe.
- Traffic Shaping: In some cases, rather than completely blocking excessive traffic, you can “shape” or slow it down to maintain performance without overwhelming the server.
4. Application-Layer Filtering And Protection
An Advanced WAF operates at the application layer, meaning it specifically protects the functionality of your web apps. This layer of protection is especially important against SQL Injection and Cross-Site Scripting (XSS) attacks, which exploit vulnerabilities in the code.
- Request Inspection: Your WAF will inspect each request to ensure it’s legitimate and doesn’t contain harmful code.
- Blocking Common Vulnerability Exploits: Preconfigured filters can block well-known application vulnerabilities such as OWASP Top 10 threats.
5. SSL/TLS Encryption Handling
SSL/TLS encryption ensures that data passed between a user and a website is secure. However, SSL traffic can sometimes hide malicious activity from less advanced security systems. An Advanced Web Application Firewall can inspect SSL traffic without compromising the encryption, providing full visibility into potential threats.
- SSL Offloading: Offloading SSL processing to your WAF improves performance by reducing the load on your servers.
- SSL Traffic Inspection: Advanced WAFs can decrypt and inspect traffic, ensuring no malicious content is hidden within encrypted data streams.
These core configurations ensure that your Advanced Web Application Firewall can provide a high level of security tailored to the needs of your web application.
Common Mistakes to Avoid in WAF Configurations
Configuring an advanced web application firewall can significantly boost your website’s security, but if done incorrectly, it can lead to vulnerabilities or unnecessary complications. Here are some common mistakes to avoid when configuring your WAF:
1. Misconfiguring or Over-configuring the WAF
One of the most common mistakes is either misconfiguring or over-configuring the WAF. If your configuration is too loose, attackers can find vulnerabilities and exploit them. If it’s too strict, you might end up blocking legitimate users or services, which can frustrate customers and harm your website’s performance.
To avoid this, start with a balanced configuration. Use default settings as a baseline, and then gradually customize the rules based on the traffic patterns and types of threats your site encounters.
2. Failing to Update Rule Sets Regularly
Cyber threats are always evolving, and if your WAF isn’t regularly updated, it will quickly fall behind. A common mistake is failing to enable dynamic rule updates, which allows the WAF to automatically receive the latest threat intelligence and adjust its defenses accordingly.
Make sure your advanced web application firewall is set to update rule sets in real-time, and manually check for updates from your WAF provider periodically.
3. Not Monitoring WAF Performance Regularly
Another mistake is the “set it and forget it” approach. After configuring the WAF, many administrators neglect to monitor its performance. Regular monitoring is essential because it helps you identify abnormal traffic patterns, potential weaknesses, and new attack vectors.
Use WAF logs and analytics tools to continuously review how well the firewall is performing. Adjust the settings if you notice unusual activities, such as repeated login attempts, high bot traffic, or unexpected spikes in specific regions.
4. Overlooking Application-Specific Threats
Not all websites face the same threats. A mistake many site owners make is assuming that all WAF settings apply universally. For example, if your site hosts sensitive user data, you will need stronger security against application-layer attacks like SQL injections and cross-site scripting (XSS). Failing to account for these specific threats can leave your application vulnerable.
When configuring your WAF, tailor it to your site’s specific risks. This will allow the firewall to focus on protecting your most critical areas.
5. Ignoring False Positives
A WAF may sometimes block legitimate traffic by mistake, which is known as a false positive. Ignoring these false positives can hurt your website’s performance and user experience. Regularly review your WAF’s logs to identify and correct these cases, and adjust the firewall settings accordingly to avoid blocking valid users.
How to Choose the Right WAF for Your Hosting Security
Choosing the right Advanced Web Application Firewall (WAF) is one of the most important decisions you can make for protecting your web applications. With the increasing complexity of cyber threats, your WAF should not just defend against common attacks but also adapt to emerging threats. Below are key considerations to guide you in selecting the ideal WAF for your hosting security needs.
1. Understand Your Web Application’s Security Needs
The first step in choosing the right WAF is assessing your specific security requirements. Every web application faces different threats based on its functionality, user base, and the types of data it handles. For instance, an e-commerce site that processes credit card payments will need robust protection against SQL injection and cross-site scripting (XSS) attacks, while a content-heavy site may need bot management to prevent scraping and spam. Conducting a security assessment of your application helps determine the types of threats you need protection from.
2. Decide on Deployment Type: Cloud, On-Premises, or Hybrid
There are three primary deployment models for Advanced WAFs: cloud-based, on-premises, and hybrid. Each comes with its advantages and disadvantages.
- Cloud-based WAFs are hosted by third-party providers, making them easy to set up, highly scalable, and cost-effective. These are ideal for businesses that require rapid deployment without the hassle of managing hardware.
- On-premises WAFs provide greater control over customization and integration with existing network security systems. They are suited for larger enterprises with more complex infrastructure but come with higher upfront costs and maintenance responsibilities.
- Hybrid WAFs combine cloud and on-premises elements, allowing you to leverage the scalability of cloud services while retaining some control over specific security components.
3. Consider Ease of Management And Customization
A WAF should be easy to manage while offering the flexibility to customize security rules according to your application’s needs. Look for a WAF solution with an intuitive user interface, real-time reporting, and actionable alerts. It should allow for rule customization so that you can tailor it to the traffic patterns and vulnerabilities of your application.
Also, make sure the WAF supports automatic updates to keep up with the latest security threats. Some advanced WAFs integrate AI and machine learning features, which enable them to automatically adapt and block emerging threats without requiring manual input.
4. Focus on Comprehensive Threat Protection
Your WAF should be able to protect against a wide range of attacks, including:
- Layer 7 Attacks: Look for a WAF that protects at the application layer (Layer 7) to guard against attacks like SQL injection, XSS, and cross-site request forgery (CSRF).
- Bot Management: Ensure the WAF can differentiate between legitimate bots (such as search engine crawlers) and malicious bots that attempt data scraping or account takeover attacks.
- DDoS Protection: Distributed Denial of Service attacks can cripple your website by overwhelming it with traffic. A WAF with built-in DDoS mitigation ensures your site stays online during high-traffic attack events.
- Virtual Patching: This feature can block threats that target known vulnerabilities, giving you time to apply actual patches to your web applications.
5. Scalability And Performance
As your application grows, so will its traffic volume, which means you will need a WAF that can scale alongside your business. Cloud-based WAFs typically offer the best scalability, allowing you to increase resources during traffic spikes. However, even the best WAF can negatively impact performance if not optimized, so be sure to choose a solution that introduces minimal latency.
6. Compliance And Certifications
Your WAF should meet industry standards and certifications that align with your business’s compliance requirements. For example, if your website handles payment transactions, the WAF should comply with PCI DSS. Businesses operating in regions with strict data protection laws, such as Europe, must also ensure their WAF is compliant with GDPR. Check for certifications like ISO/IEC 27001, which guarantees that the WAF provider adheres to international security standards.
7. Cost And Support
Lastly, weigh the cost of the WAF against its features and your budget. Most providers offer tiered pricing based on traffic volume, security features, and the number of protected applications. Look for a WAF that offers the best value without sacrificing key security functions. Additionally, reliable customer support is crucial. You should choose a provider that offers 24/7 support in case of a security incident or technical issue.
By considering these factors, you can choose an Advanced Web Application Firewall that best suits your hosting security needs, providing strong, adaptable, and scalable protection.
Securing Your Web Application Easily with Advanced WAF Configurations
An Advanced Web Application Firewall (WAF) is a crucial tool in safeguarding web applications against modern cyber threats. Its ability to provide real-time protection, adapt to emerging vulnerabilities, and offer tailored configurations for various hosting environments ensures robust security. Investing time in configuring and automating your WAF properly will protect your web applications and secure your digital presence in today’s threat landscape.
If you have found this blog helpful, feel free to subscribe to our blogs for valuable tutorials, guides, knowledge, and tips on web hosting and server management. You can also join our Facebook community to share insights and engage in discussions.