Ever worried about your website getting hacked? You are not alone. Website vulnerability checkers are your digital shields, spotting weak points before hackers do. They are like having a 24/7 security team but for your online presence. You are not just protecting your site – you are safeguarding your business and customer trust. In this blog, we will be exploring why you should start using a website vulnerability checker in xCloud and take control of your website’s security.
Deeper Dive into Website Vulnerabilities
Website vulnerabilities are weaknesses or misconfigurations in website design, implementation, or operation that attackers can exploit. These vulnerabilities can compromise a website’s integrity, availability, or confidentiality, affecting its code, server configuration, database, and third-party plugins or extensions.
Definition And Types of Common Website Vulnerabilities
Here are a few major ones to consider when it comes to defining the types of website vulnerabilities:
- SQL Injection: SQL injection is a prevalent web application vulnerability where attackers insert malicious SQL code into input fields to manipulate a website’s database. This can lead to unauthorized data access or manipulation, allowing attackers to create, read, alter, or delete data stored in the database.
- Cross-Site Scripting (XSS): XSS vulnerabilities occur when attackers inject scripts, often JavaScript, into web applications. These scripts are executed in the victim’s browser, enabling attackers to hijack user sessions, deface websites, or redirect users to malicious sites.
- Remote Code Execution (RCE): RCE vulnerabilities allow attackers to execute arbitrary code on a target server or application. This can lead to complete control over the affected system, enabling data theft, system manipulation, or further network penetration.
- Cross-Site Request Forgery (CSRF): CSRF attacks trick authenticated users into performing unintended actions on a website. Attackers exploit CSRF vulnerabilities to perform unauthorized actions, such as changing user passwords or transferring funds.
- Directory Traversal: Directory traversal vulnerabilities enable attackers to access restricted directories and execute commands outside the web server’s root directory. This can expose sensitive files and data, leading to unauthorized access and potential data breaches.
Impact of Vulnerabilities on Website Security And User Data
Website vulnerabilities pose significant threats to security and user data. In fact, 55.9% of the attacks on WordPress are due to vulnerable plugins They can lead to unauthorized access to sensitive information, such as personal data, financial details, and login credentials. When exploited, these vulnerabilities can compromise the integrity of the entire website, damaging its reputation and affecting the business’s bottom line.
For instance, SQL injection attacks can result in data breaches, exposing user credentials and other sensitive information. XSS attacks can hijack user sessions, leading to unauthorized transactions or data theft. CSRF vulnerabilities can be exploited to perform actions without the user’s consent, potentially leading to financial loss or data manipulation.
Features of an Effective Website Vulnerability Checker
Understanding the key features of an effective website vulnerability checker is crucial for maintaining robust web security. Here, we delve into the essential components that make these tools effective.
Comprehensive Scanning Capabilities
An effective website vulnerability checker must possess comprehensive scanning capabilities. This means it should be able to detect a wide range of vulnerabilities, including common threats like SQL injections, Cross-Site Scripting (XSS), and Distributed Denial of Service (DDoS) attacks. The tool should also be regularly updated to identify new and emerging threats, ensuring that it remains effective against the latest security challenges. Automated web vulnerability scanning tools are particularly beneficial as they can quickly crawl large volumes of web pages without interruptions, making them highly efficient.
User-Friendly Interface
A user-friendly interface is essential for a website vulnerability checker to be effective. Users should be able to navigate the tool easily and understand the instructions without confusion. This includes having a clean layout, intuitive navigation, and clear instructions that guide users through the scanning process. A straightforward interface ensures that users can efficiently operate the tool and interpret the results, even if they are not security experts.
Detailed Reporting
Detailed reporting is another critical feature. An effective website vulnerability checker should provide comprehensive reports that include steps to reproduce and fix identified vulnerabilities. This not only helps users understand the nature of the vulnerabilities but also provides actionable insights for remediation. Detailed documentation and reporting are essential for developers to quickly address and fix issues, thereby enhancing the security posture of their website.
Integration Capabilities
Integration capabilities are vital for a website vulnerability checker to seamlessly fit into an organization’s existing security infrastructure. The tool should be compatible with various platforms and tools, allowing for seamless integration into the Software Development Lifecycle (SDLC) and other security workflows. This ensures that vulnerabilities are identified and addressed early in the development process, reducing the risk of security breaches.
Automated Scanning And Alerts
Automated scanning and real-time alerts are crucial for keeping users informed of potential threats. An effective website vulnerability checker should allow users to schedule scans and receive alerts whenever a new vulnerability is detected. This proactive approach helps organizations stay ahead of potential threats and ensures that vulnerabilities are addressed promptly before they can be exploited by attackers.
How to Choose the Right Website Vulnerability Checker
Selecting the right website vulnerability checker is crucial for maintaining the security and integrity of your online presence. Here is a detailed guide to help you make an informed decision.
Assessing Your Needs
Understanding your specific security requirements and potential threats is the first step in choosing a website vulnerability checker. Different websites have varying levels of exposure to threats based on their size, the sensitivity of data handled, and the nature of their operations. For example, an e-commerce site handling credit card transactions will have different security needs compared to a personal blog. It is essential to identify the types of data you need to protect and the potential threats you face, such as SQL injection or cross-site scripting (XSS).
Evaluating Features
Once you have assessed your needs, the next step is to evaluate the features of different vulnerability-checking tools. Look for tools that offer comprehensive scanning capabilities, including the ability to detect both common and complex vulnerabilities. Features such as authenticated scanning, which allows the tool to check behind login pages, and the ability to handle JavaScript-heavy websites are important. Tools that offer a low rate of false positives and provide detailed reports with remediation recommendations can save time and resources.
How to Check Vulnerability Issues from Server End & Fix Accordingly?
With xCloud you can perform the following Vulnerability Issues from Server End and fix them as required. To do so, follow these steps:
Step 1: Enable Vulnerability Checker
Once you are logged into your xCloud dashboard, go to ‘Servers’ and choose one of your servers if you have more than one. You will see a list of all the sites hosted on that server.
Next, click on ‘Security’ and look for the ‘Vulnerability Scan’ section. Turn on the switch next to ‘Enable Vulnerability Scan.’ If you want to automatically update any vulnerability issues, turn on the switch for ‘Enable Auto Update.’ Do not forget to click ‘Save Settings’ after making these changes.
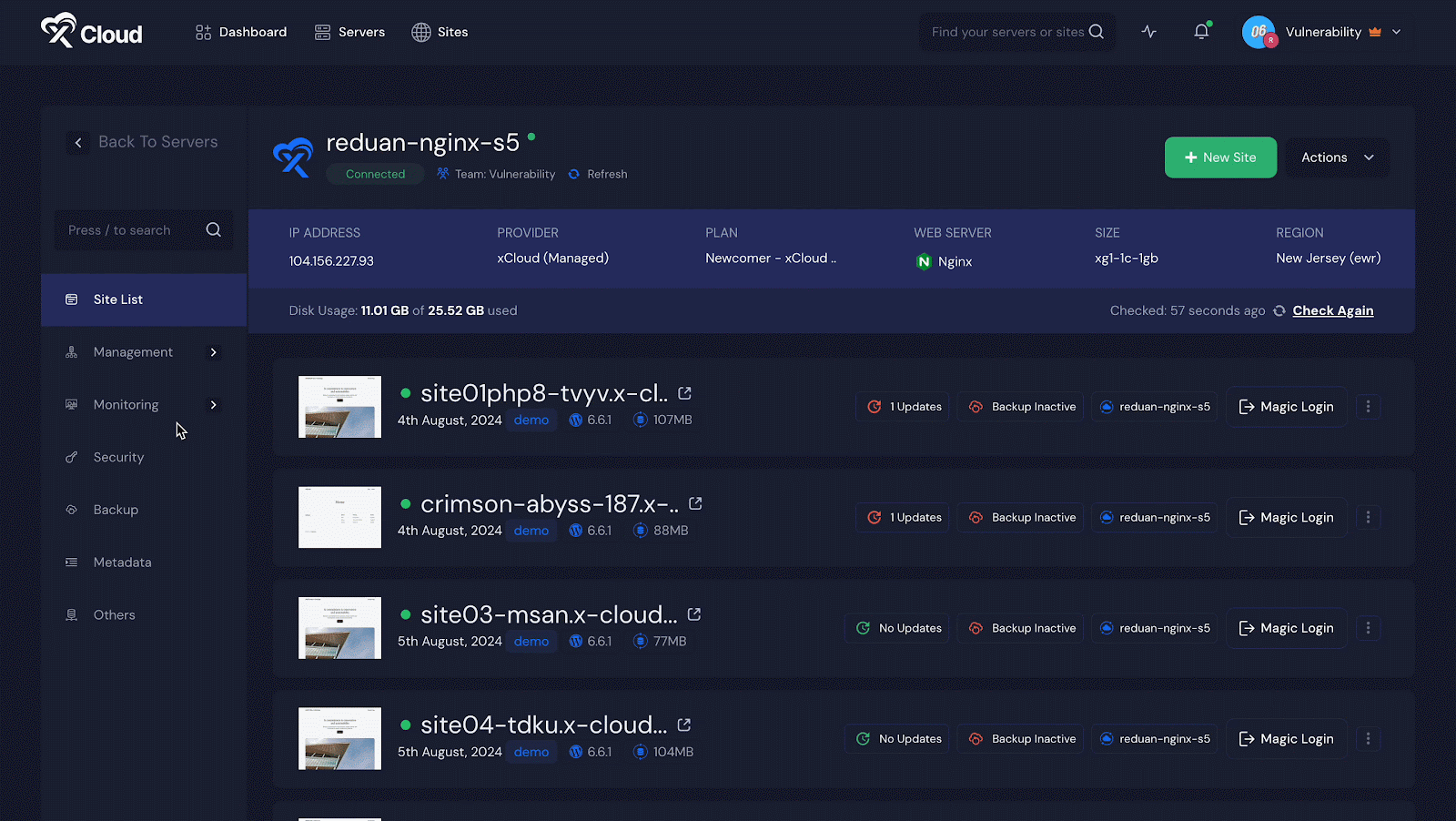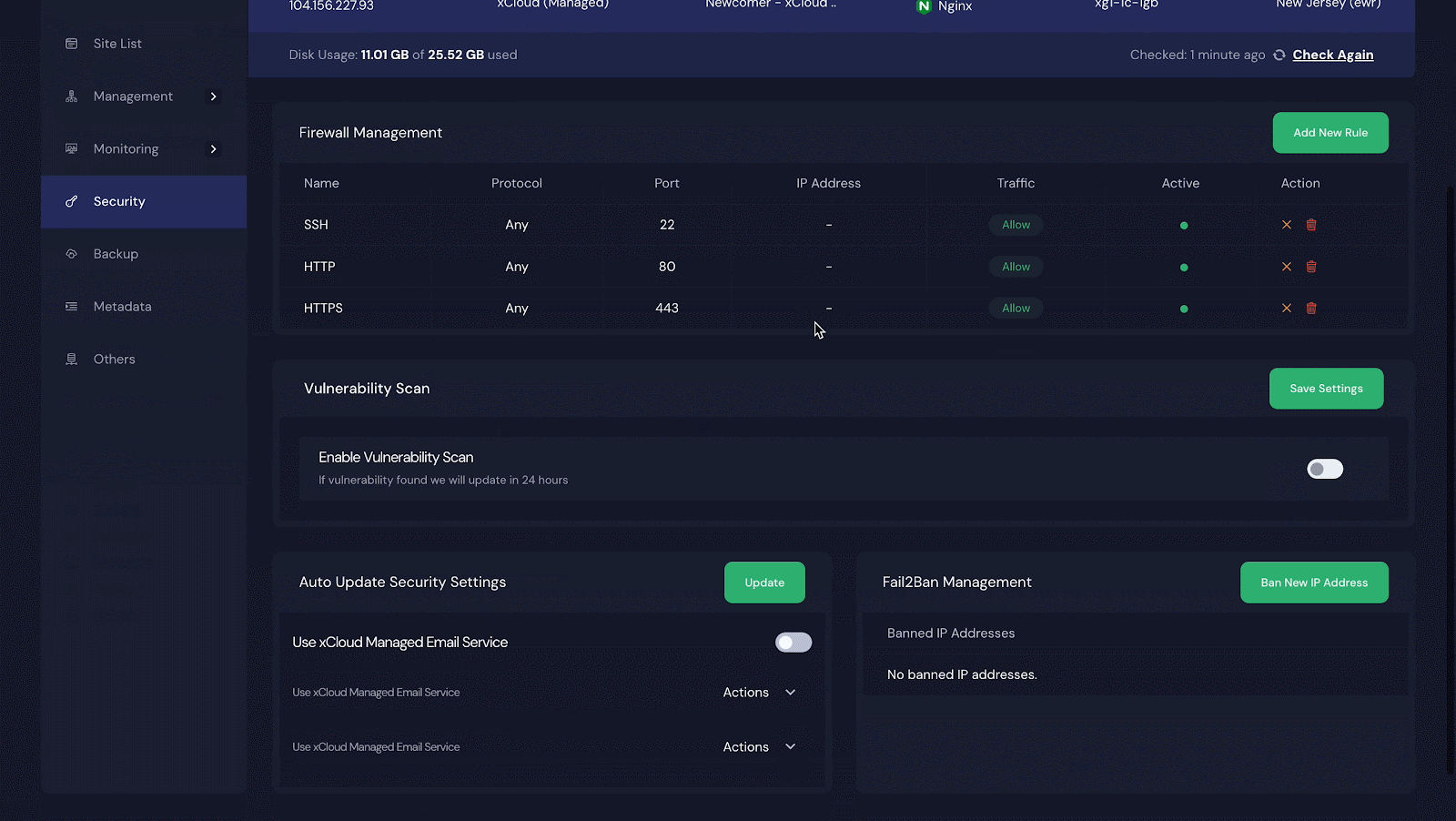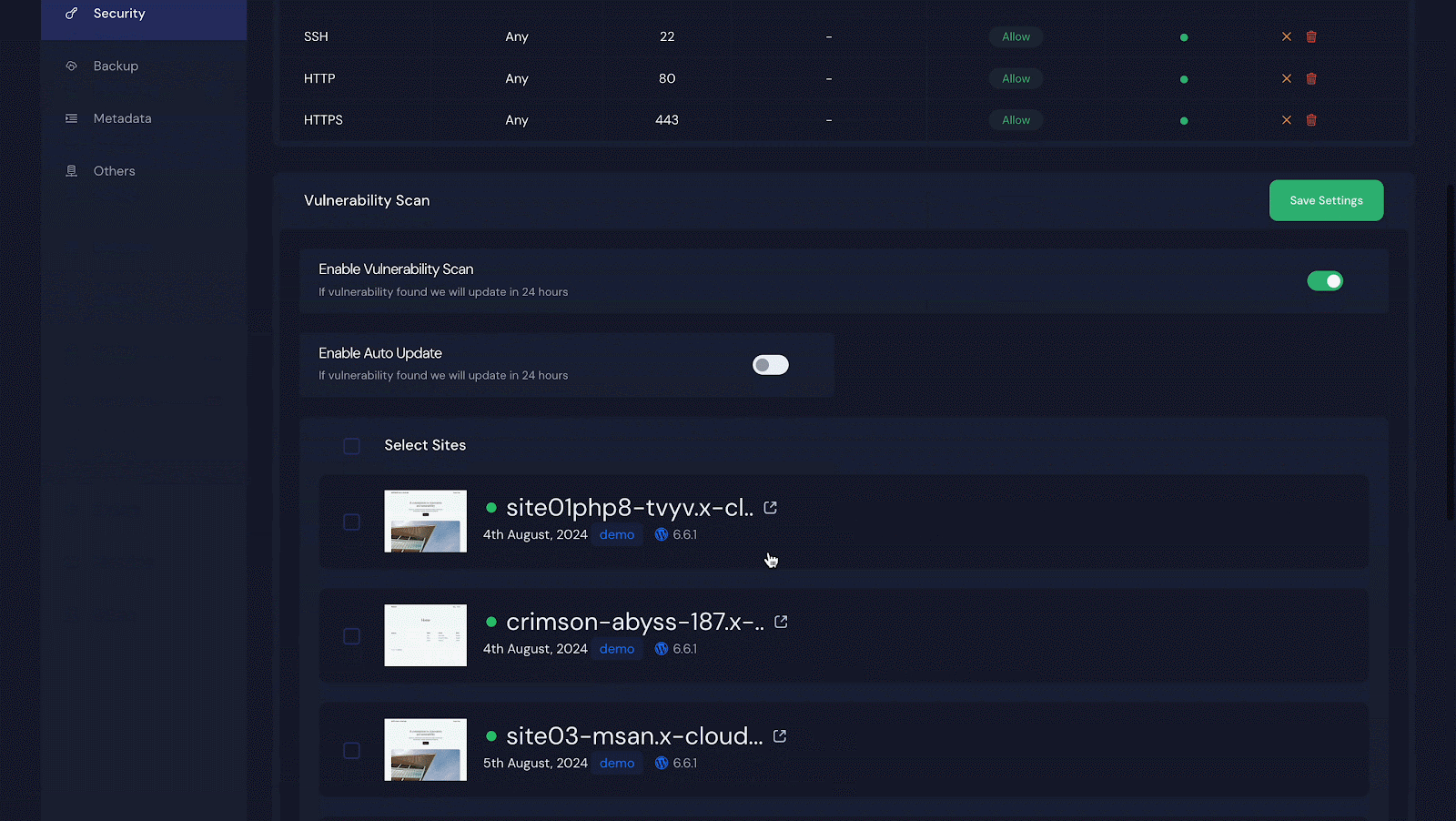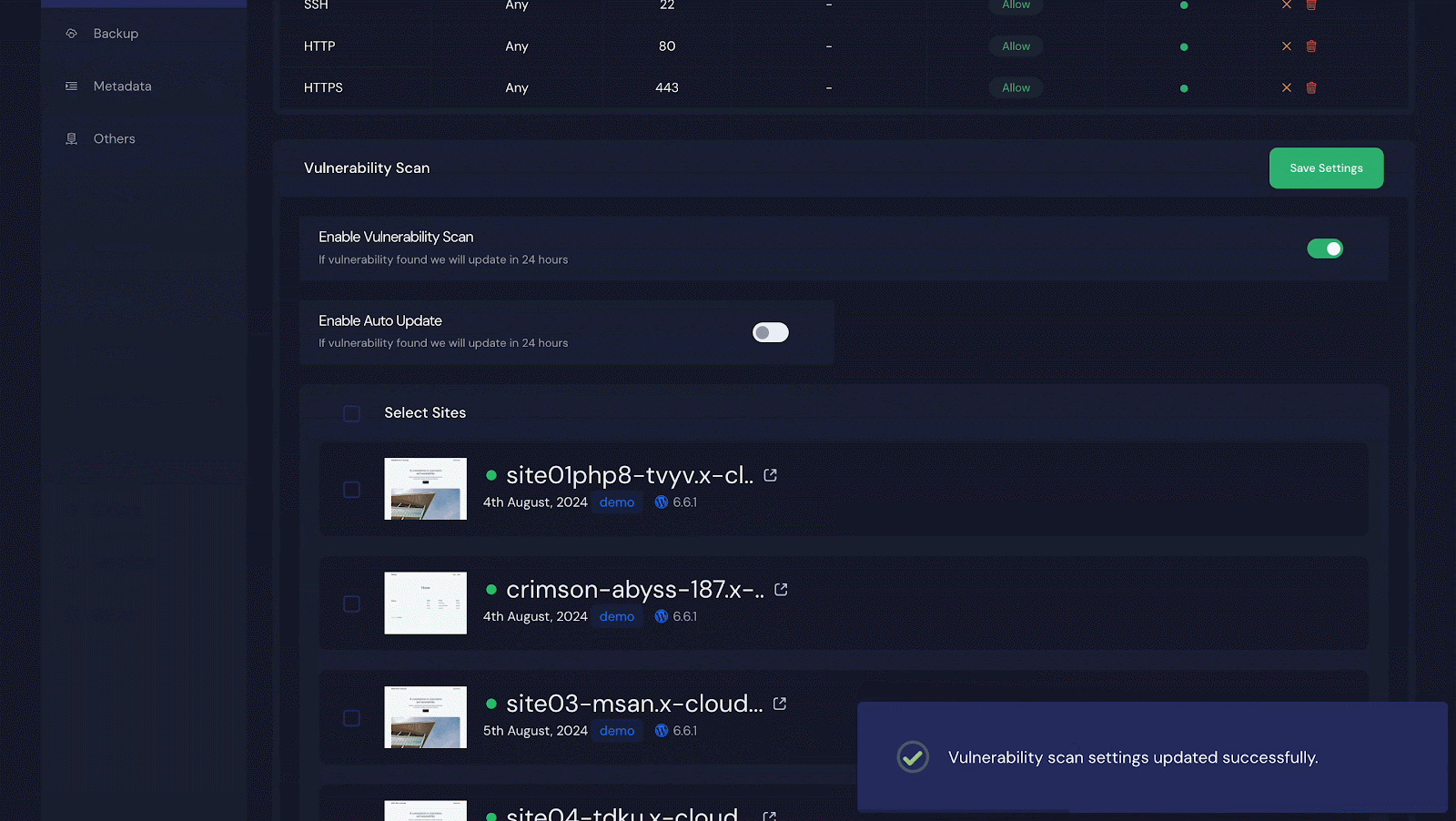
Step 2: Select Sites to Get the Vulnerability Issues
To receive vulnerability notifications for all your sites, click ‘Select Sites’ at the top to select them all. For specific sites, select only those and click ‘Save Settings’.
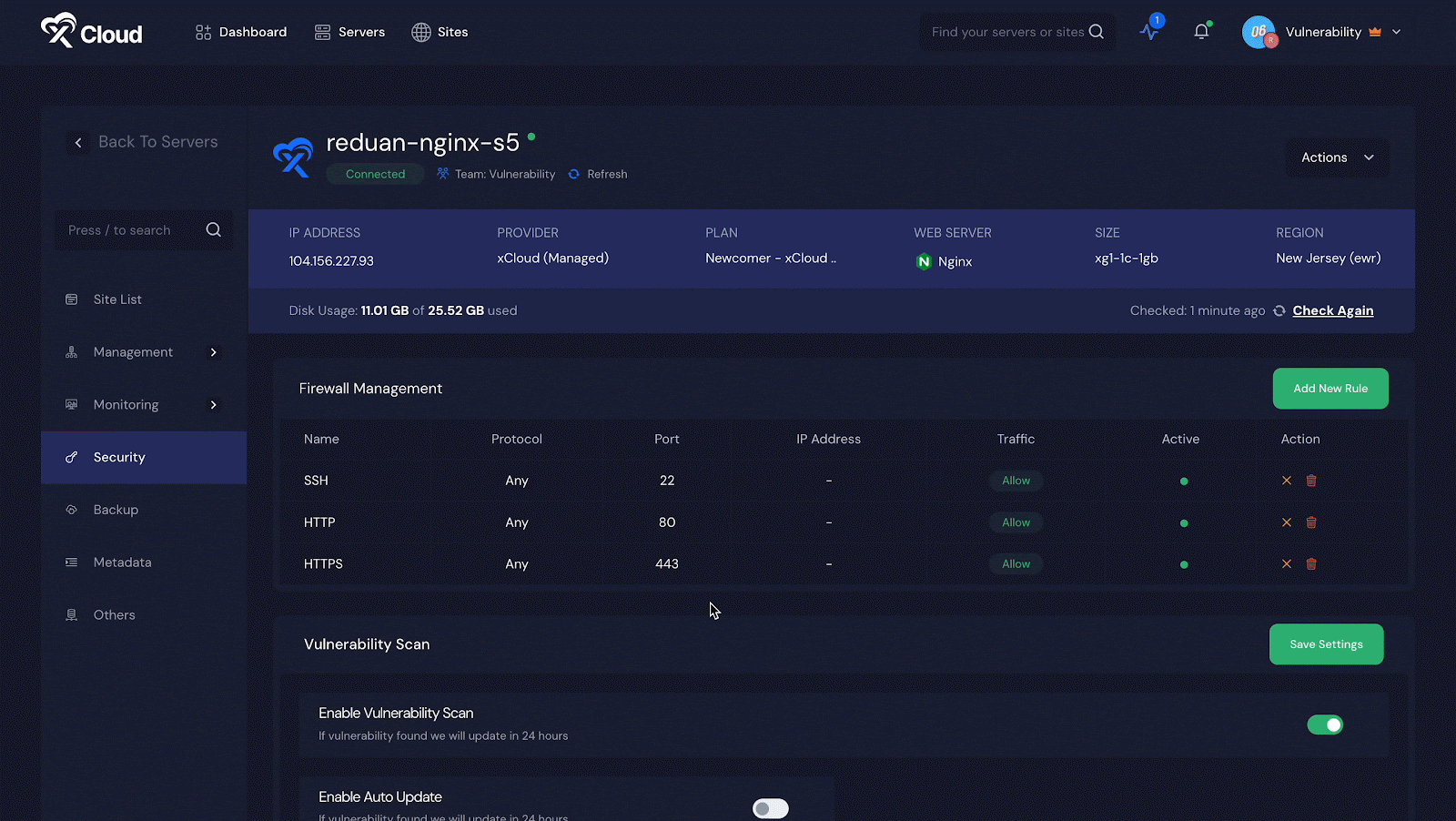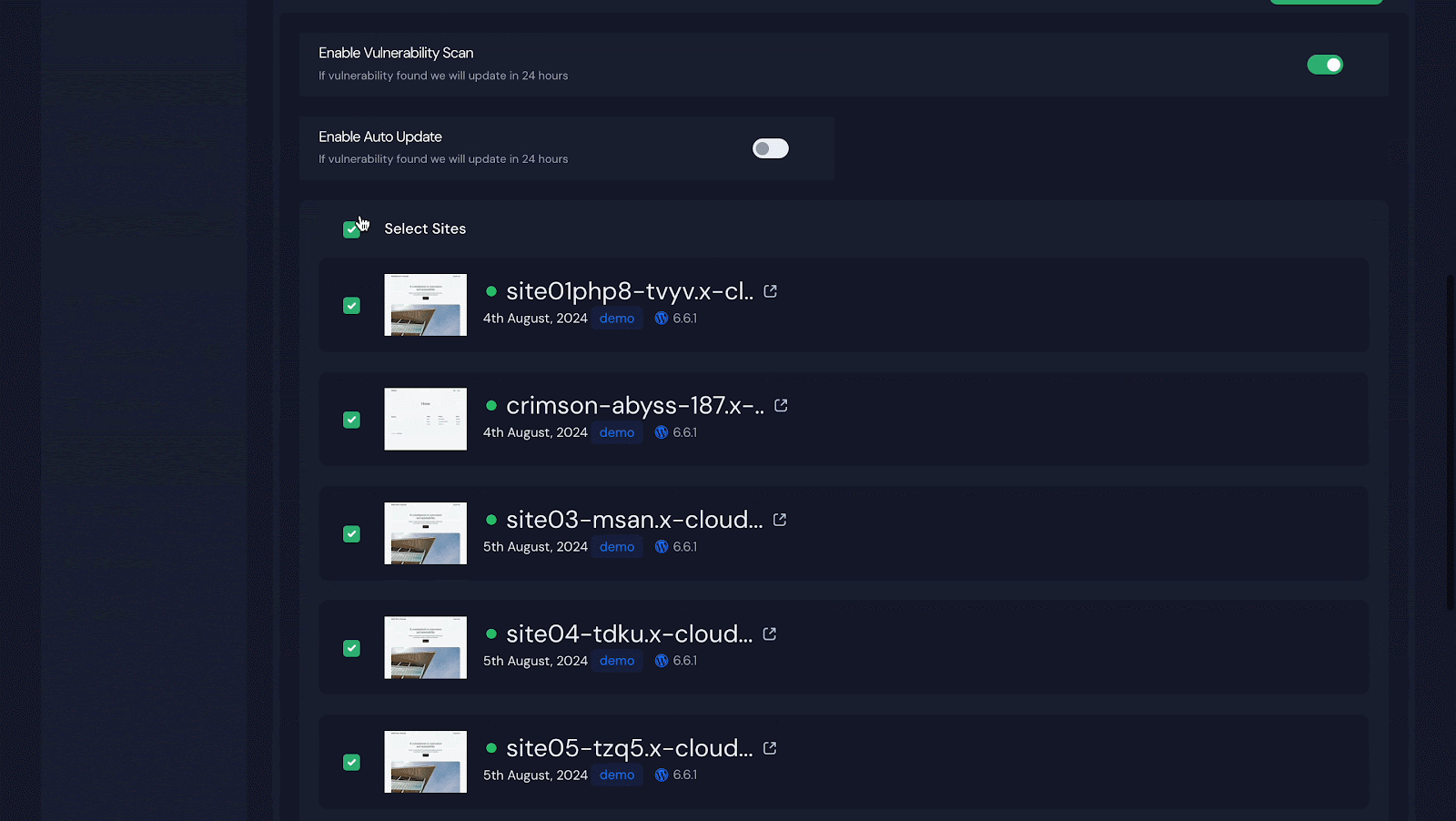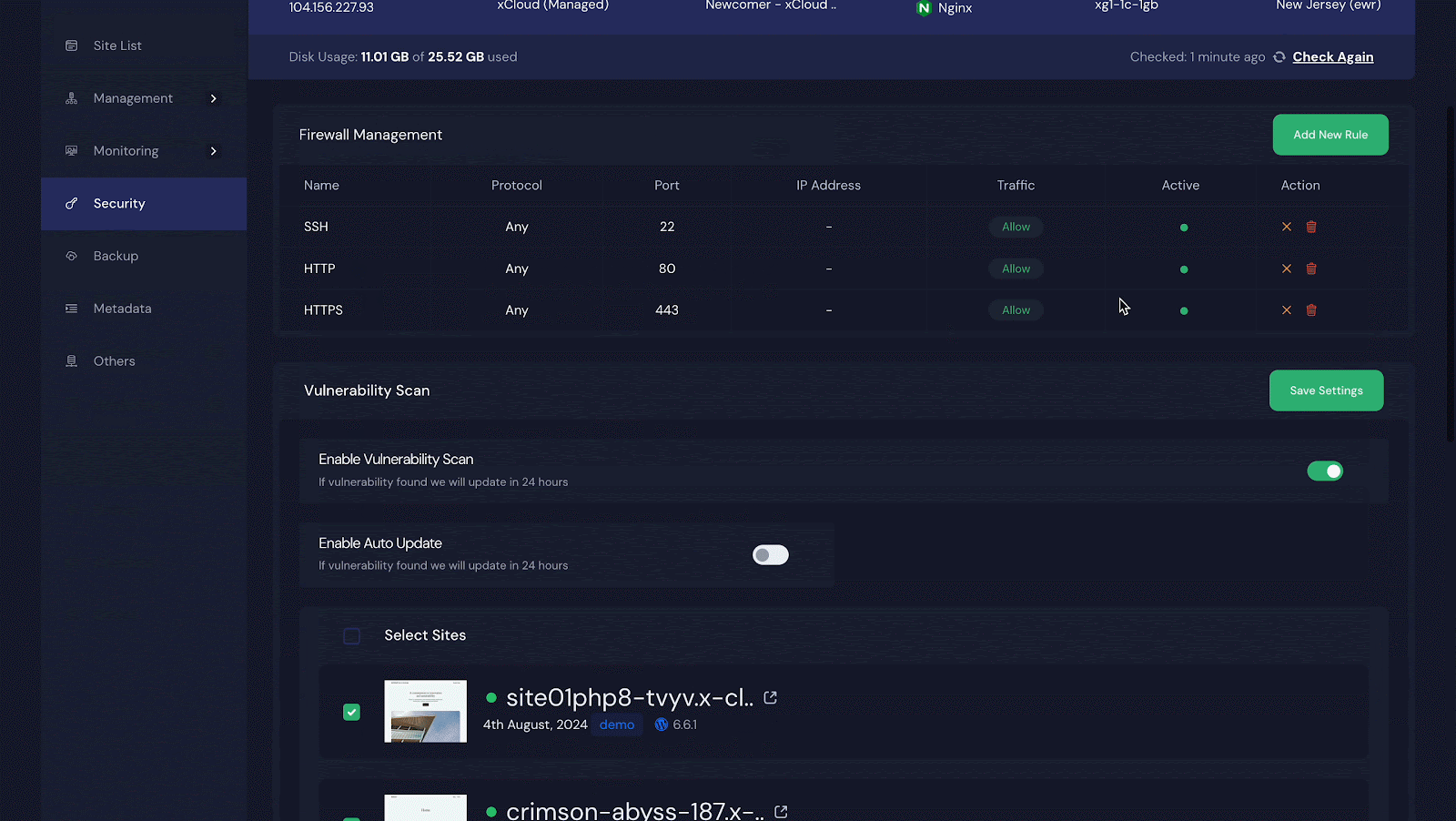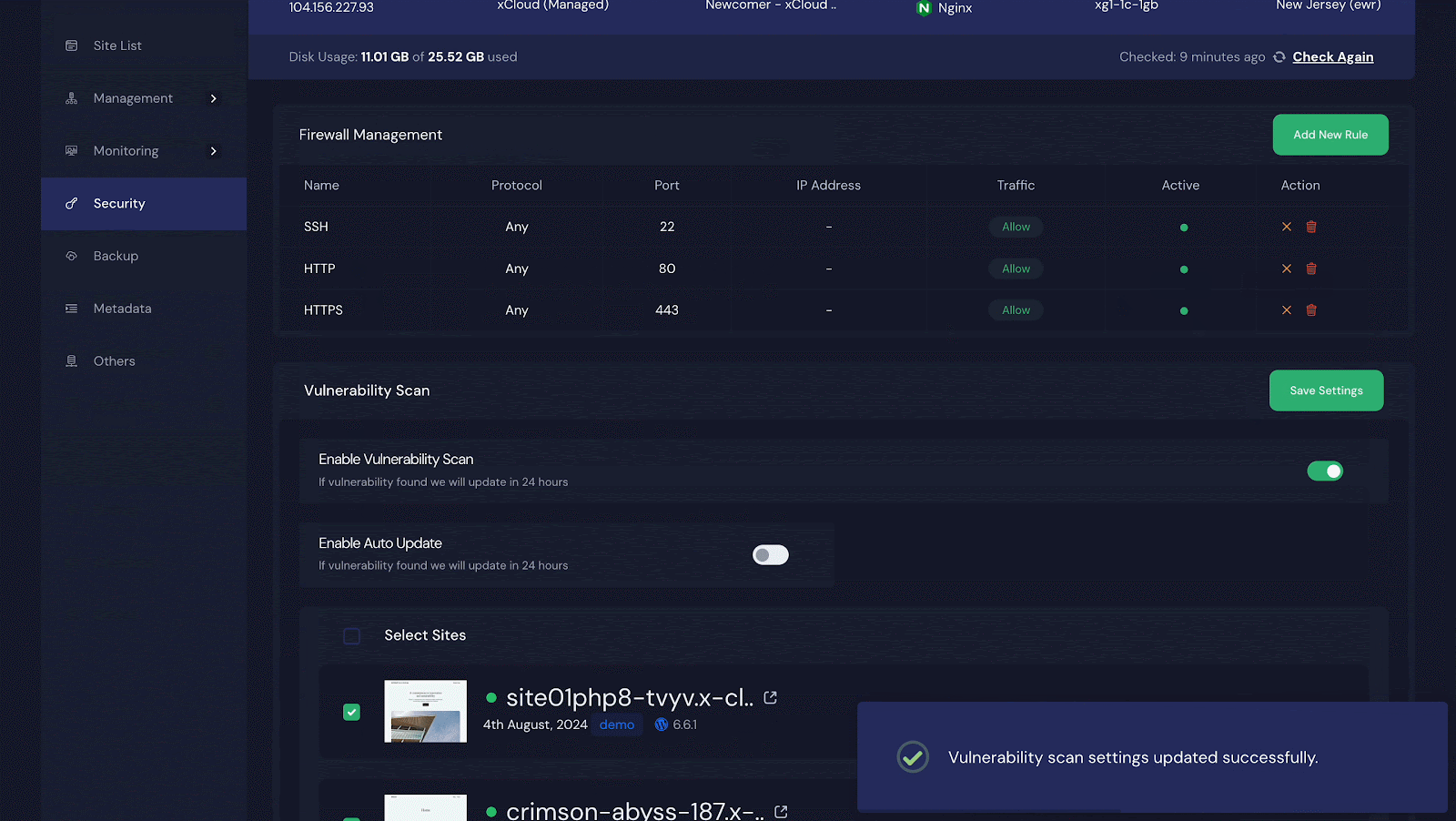
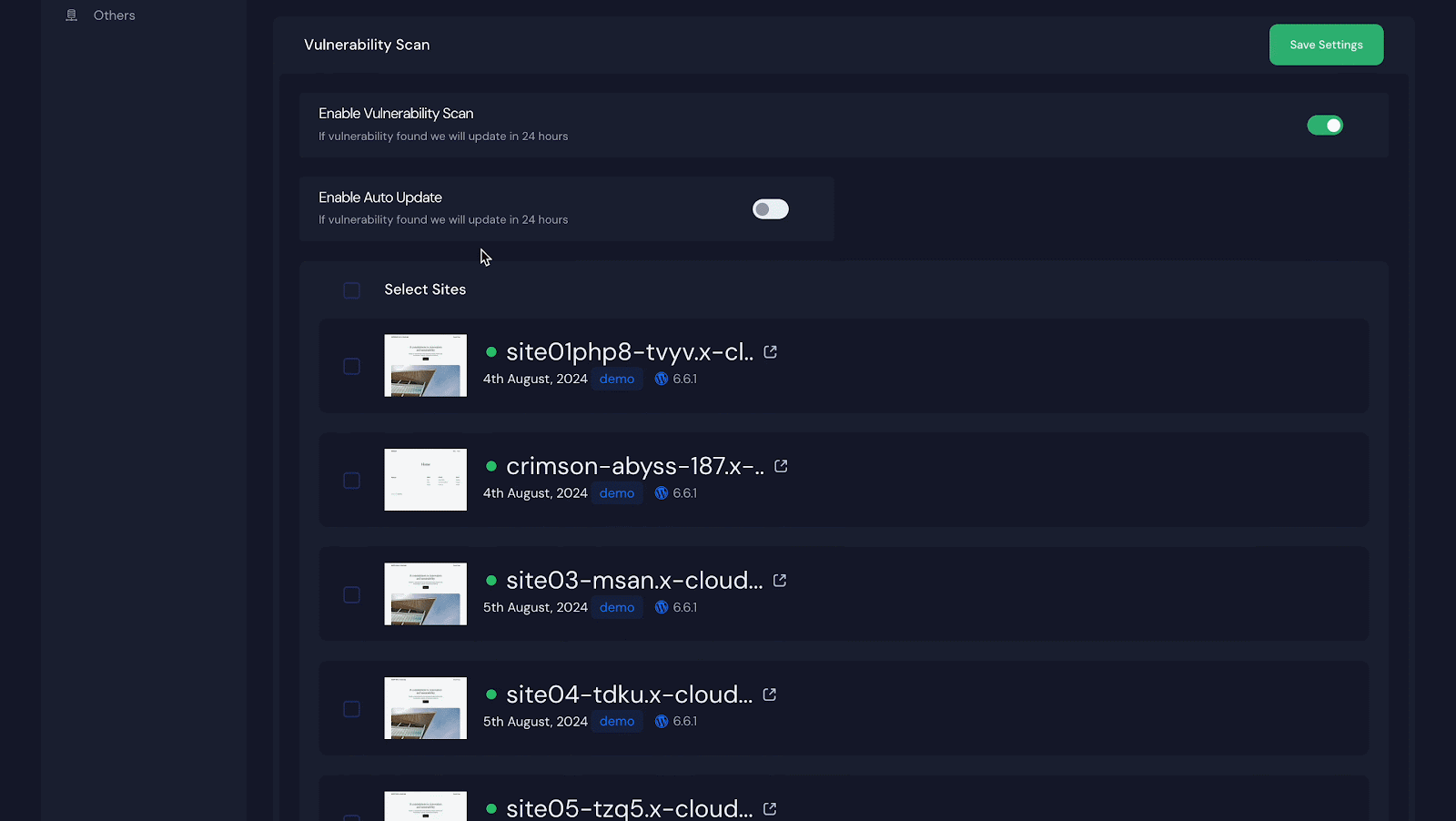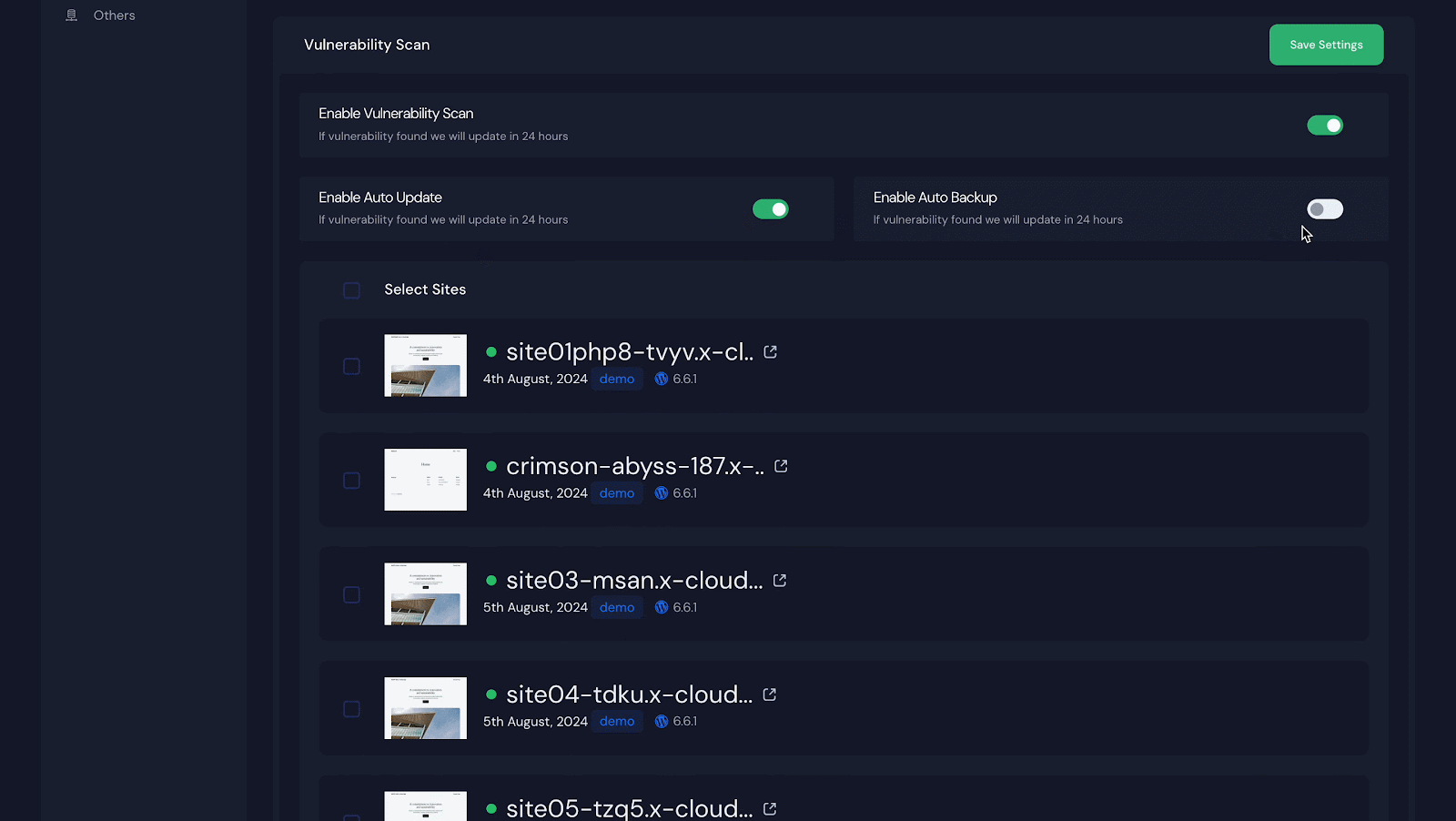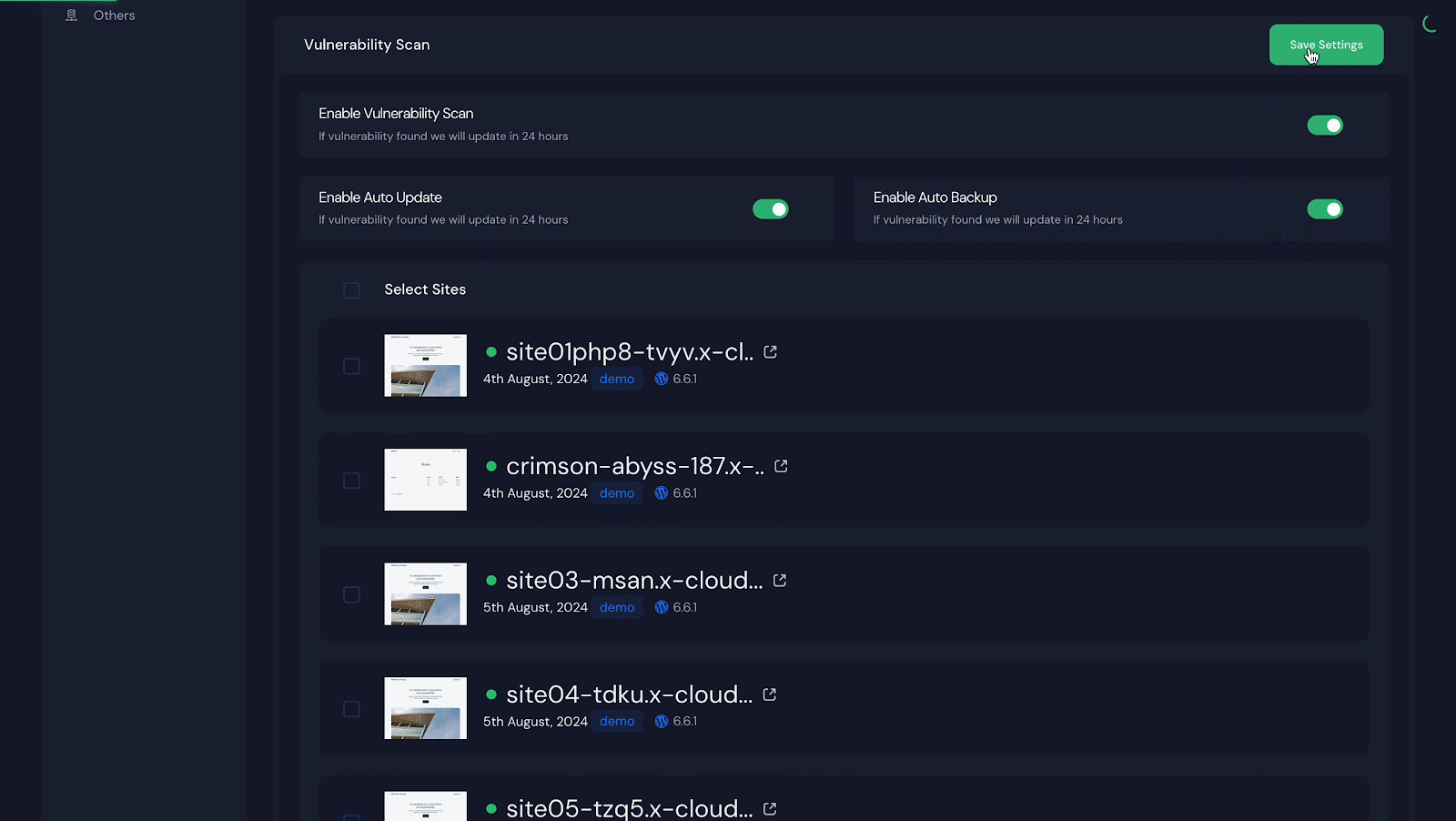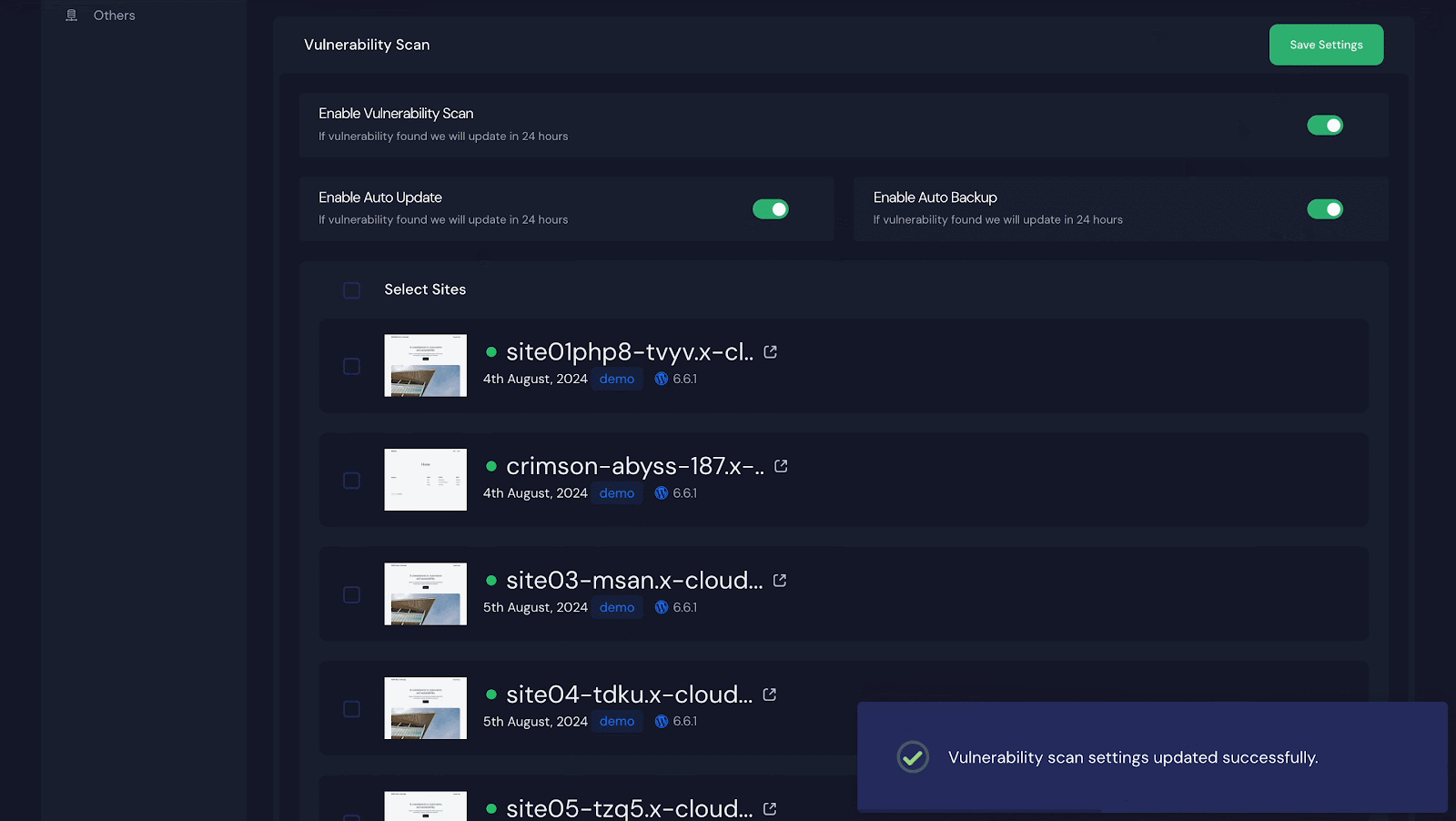
Step 3: Enabling Auto Update & Auto Backup
Turning on ‘Auto Update’ reveals an ‘Enable Auto Backup’ option. To back up everything automatically, toggle it on and click ‘Save Settings.’
For more information, you can check our detailed documentation.
xCloud Vulnerability Checker
The xCloud vulnerability checker stands out for its robust features and effectiveness in identifying website vulnerabilities. It offers comprehensive scanning capabilities, ensuring
a wide range of vulnerabilities are detected and addressed. The tool’s user-friendly interface makes it accessible to users of all expertise levels, while its detailed reporting provides actionable insights for remediation.
xCloud’s integration capabilities allow it to seamlessly fit into various security workflows, enhancing its usability across different platforms. With automated scanning and real-time alerts, xCloud ensures that users are always informed of potential threats, making it a reliable choice for maintaining website security.
If you have found this blog helpful, feel free to subscribe to our blogs for valuable tutorials, guides, knowledge, and tips on web hosting and server management. You can also join our Facebook community to share insights and engage in discussions.