Web application security is getting more and more important with the rapidly evolving technology. Website owners need robust security measures to protect their web apps and sensitive data with the increasing number of cyber threats.
One powerful tool for enhancing web app security is Cloudflare which is a Google product. Cloudflare provides an array of services designed to improve website performance, security, and safeguarding web applications. Today, we will explore how Cloudflare firewall rules can help secure your web app and best practices to protect your web applications without any hassle.
🍀Understanding Cloudflare Firewall Rules
Web application security is important nowadays. With ever-evolving cyber threats, having a reliable line of defence is essential. This is where Cloudflare firewall rules come into play. Let us discuss what firewall rules are, how they work, and why they are vital for securing your web app.
🔆What Are Cloudflare Firewall Rules?
Cloudflare firewall rules are a powerful set of configurations that allow you to define precise security measures for incoming traffic to your web application. These rules act as filters that control which requests can access your site based on specific conditions you set. By utilizing these rules, you can manage and mitigate various types of threats, enhancing the security of your web application.

🔆How Do Cloudflare Firewall Rules Work?
Cloudflare firewall rules operate at the application layer of the Open Systems Interconnection (OSI) model. This means they focus on the specifics of incoming HTTP requests to your site, allowing you to filter traffic based on criteria such as IP address, country of origin, URL patterns, and more.
When a request is made to your site, the firewall rules are evaluated sequentially based on their priority. Each rule consists of a matching condition and an action to perform if the condition is met. Actions can include allowing, blocking, challenging, or logging the request.
🔆Why Use Cloudflare Firewall Rules for Web App Security?
Firewall rules is an effective way to secure your web application with setting up rules to secure your web applications for several reasons:
- Granular Control: The rules allow you to create highly specific conditions, giving you granular control over the traffic that reaches your site.
- Scalability: Cloudflare’s infrastructure is built to handle massive amounts of traffic, making their firewall rules scalable for websites of all sizes.
- Performance: The rules are evaluated at Cloudflare’s edge servers, which means they do not affect your site’s performance.
- Ease of Use: Cloudflare provides an intuitive user interface and extensive documentation, making it easy to set up and manage firewall rules.
Firewall rules offer a robust and flexible solution for web app security, providing website owners with the tools they need to protect their sites from malicious traffic and other potential threats.
3 Easy Steps Guide to Set Up Cloudflare Firewall Rules
Setting up a Cloudflare rule could be a challenging task. There are many firewall rules for WordPress. We will discuss here how to block particular countries from visiting your site. You can block one country or as many as you want. You can also allow access to your website to only one country. For example, we will block visitors from all countries except the USA. So follow the steps below:
Step 1: Log in to Cloudflare Choose Your Domain
Start with logging in to your Cloudflare dashboard. From here, choose the domain name for which you want to set up the firewall rule with Cloudflare
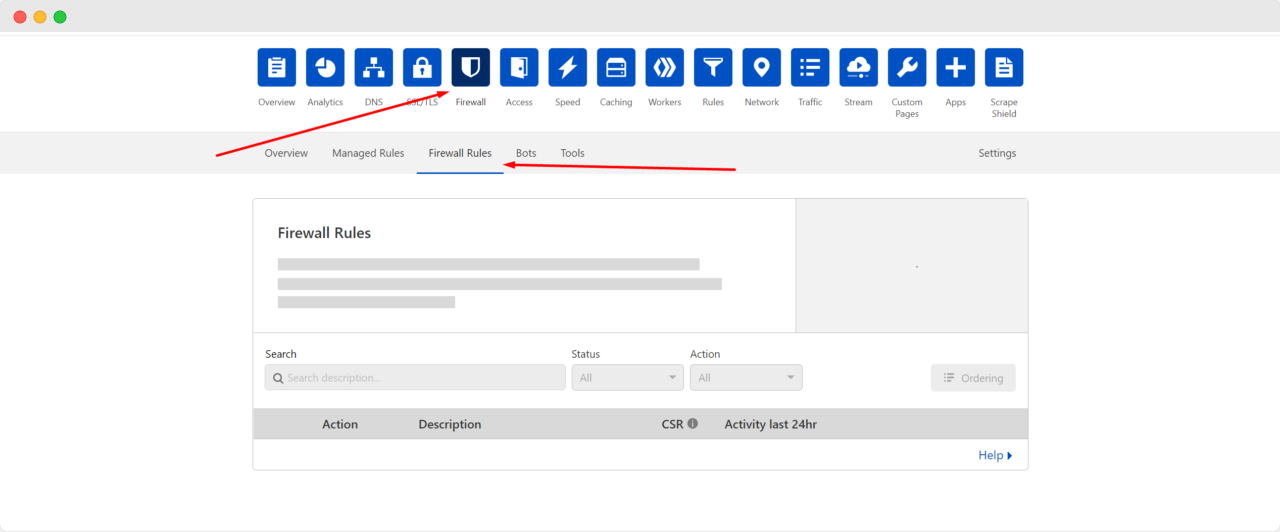
After selecting the domain that you want to secure more or applying the firewall rules, find the ‘Firewall’ button from the top bar and click on it.
Step 2: Create a Firewall Rule with Cloudflare
Here, you can see a ‘Create a Firewall rule’ button, hit on the button to create a new firewall rule.
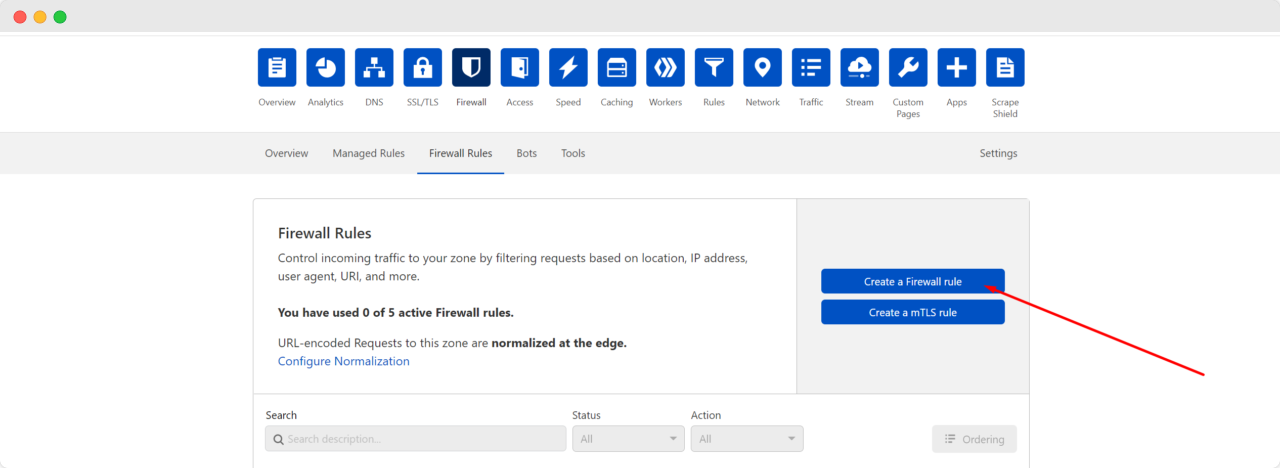
Step 3: Block All Countries Except the USA
From here, we must need to provide the necessary information. First, give a ‘Rule name’ according to your choice.
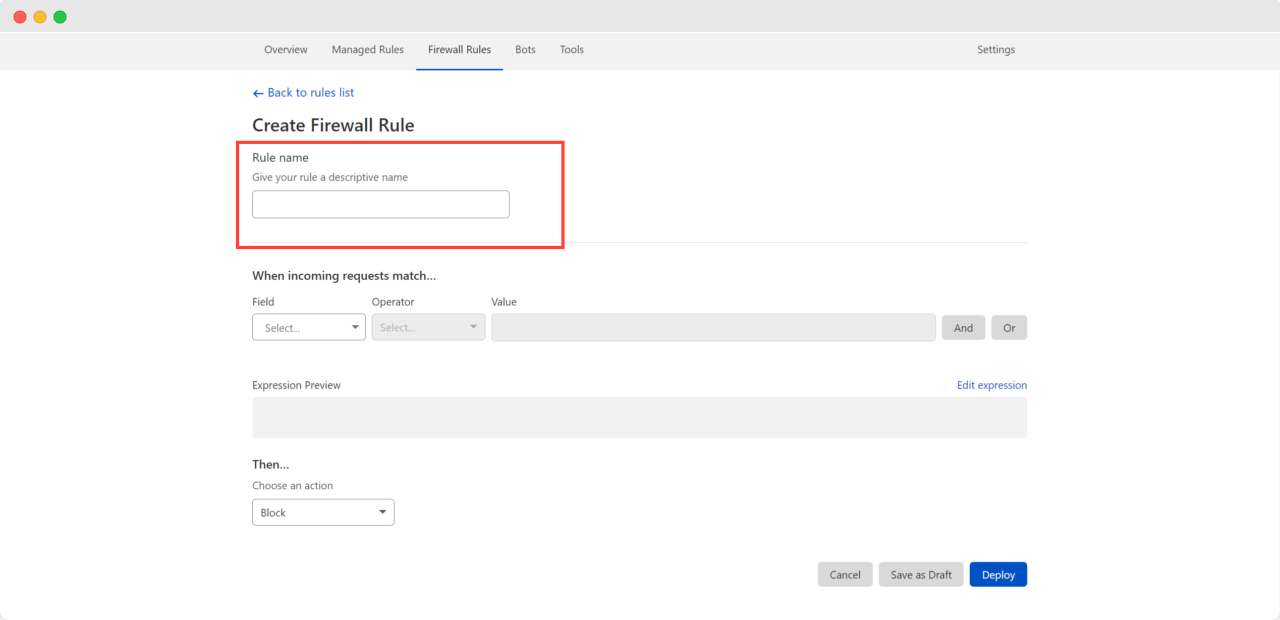
Then head on to the ‘Field’ section and choose ‘Country’ from the dropdown and set the ‘Operator’ does not equal. Next, go to the ‘Value’ and choose USA as your country.
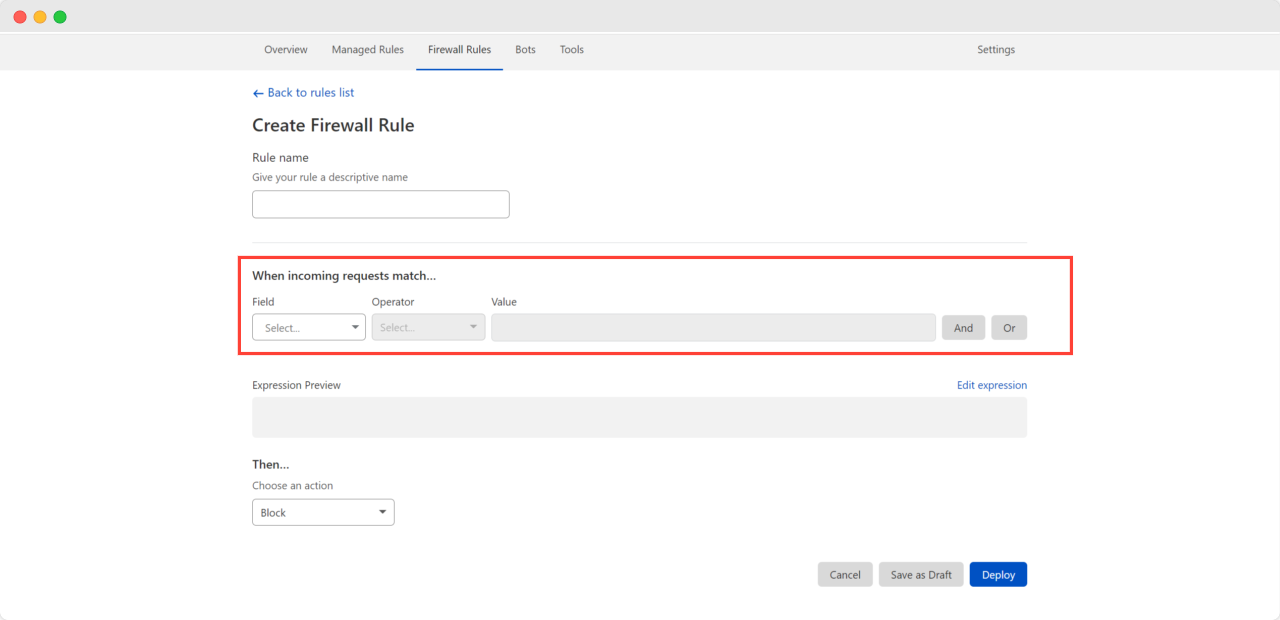
Finally, from the action drop-down, select ‘Block’, and then click on the Deploy button.
There are different types of firewall rules you can use for different purposes. You can set them up easily and make your site more secure than ever.
⛳ Benefits of Using Firewall Rules with Cloudflare
Cloudflare’s firewall rules are not just another security feature, they offer many benefits that make them an essential tool for any website owner. Let us dive into the key advantages of using firewall rules with Cloudflare to secure your web application.

🔆 Enhanced Security
Security is paramount for any web application, and Cloudflare firewall rules provide robust protection against a wide range of threats. By allowing you to set specific conditions to filter incoming traffic, the rules help defend against common attacks like DDoS, SQL injection, cross-site scripting, and more. This proactive defense mechanism ensures that your website remains secure even as threats evolve.
🔆 Ease of Use
One of the standout features of Cloudflare firewall rules is their ease of use. Cloudflare provides an intuitive dashboard that simplifies the process of creating and managing rules. Even if you are not a seasoned IT professional, you can easily set up and adjust firewall rules to suit your needs. The user-friendly interface ensures that website owners can take control of their security without needing extensive technical expertise.
🔆 Customization
Every web application is unique, and Cloudflare recognizes this by offering highly customizable firewall rules. You can set conditions based on a variety of parameters, such as IP address, HTTP methods, and country of origin. This level of customization allows you to tailor the security settings to match your specific requirements, ensuring that you only allow legitimate traffic while blocking potential threats.
🔆 Real-Time Analytics
Another significant benefit of using firewall rules is the access to real-time analytics. Cloudflare provides detailed reports on traffic and security events, allowing you to monitor and analyze incoming requests. This visibility helps you understand the nature of threats targeting your web application and adjust your security measures accordingly. The analytics also provide insights into the effectiveness of your firewall rules, enabling you to fine-tune your configurations for optimal protection.

🔆 Performance Optimization
Cloudflare’s infrastructure is designed for high performance, and the firewall rules are no exception. The rules are processed at Cloudflare’s edge servers, which means that your web application’s performance is not impacted. This edge-based processing ensures that malicious traffic is filtered out before it even reaches your server, optimizing your application’s performance while maintaining security.
🔆 Scalability
Whether you are running a small personal blog or a large e-commerce platform, Cloudflare firewall rules are scalable to meet your needs. Cloudflare’s global network is built to handle massive amounts of traffic, so you can be confident that your web application will remain secure even during traffic spikes or large-scale attacks.
⛳ Best Practices for Using Cloudflare Firewall Rules
Using firewall rules is an effective way to secure your web application, but it is essential to follow best practices to maximize their effectiveness and minimize potential issues. Here, we will discuss key strategies and tips for using firewall rules with Cloudflare effectively.
🔆 Whitelist Trusted IPs
Whitelisting trusted IP addresses ensures that your key stakeholders, such as employees or partners, always have access to your site. This is particularly useful for internal users who need consistent access. Start by identifying the IP addresses that should have unrestricted access to your web application. Once identified, create a firewall rule that allows traffic from these trusted IPs and set it as a high-priority rule. This ensures that these IPs are always permitted access, preventing unnecessary disruptions.
🔆 Block Malicious Traffic
One of the primary functions of firewall rules is to block malicious traffic. Cloudflare simplifies this by providing analytics and threat intelligence. Use Cloudflare’s tools to identify sources of malicious traffic. Based on your findings, create rules that block malicious traffic from these sources, such as specific IP addresses or user agents. This helps keep your application secure from known threats.

🔆 Rate Limiting
Rate limiting prevents abuse of your web application, such as brute force login attempts or scraping. Determine which parts of your web application are most sensitive to excessive requests, like login pages or API endpoints. Set up firewall rules to limit the number of requests per minute from a single IP address. You can choose to either block or challenge requests that exceed this limit, helping to protect your application from overload and abuse.
🔆 Monitor And Adjust Rules
Regular monitoring and adjustment of your firewall rules are crucial for maintaining optimal security. Use Cloudflare’s analytics to keep an eye on incoming traffic and spot potential issues or unusual patterns. Based on your monitoring, adjust the rules to respond to new threats or optimize existing protections. This ensures your firewall rules remain effective and up-to-date.
🔆 Leverage Managed Rulesets
Cloudflare offers managed rulesets that provide protection against common threats, such as SQL injection and cross-site scripting. In your firewall settings, enable relevant managed rulesets for your web application. If necessary, customize these rulesets to better fit your specific needs, providing tailored protection against common threats.
🔆 Test Your Rules
Before fully implementing new firewall rules, it is crucial to test them to ensure they don’t unintentionally block legitimate traffic. Cloudflare offers a preview mode that shows how the rule will behave without actually blocking or challenging traffic. When enabling new rules, monitor their effects closely and be ready to adjust them if they impact legitimate users. This cautious approach helps avoid disruptions to valid traffic.
🔆 Document Your Rules
Proper documentation of your firewall rules helps maintain clarity and facilitates future adjustments. Give each rule a descriptive name that reflects its purpose. Document the conditions and actions of each rule, as well as the rationale behind them. This makes it easier to manage and update your firewall rules over time.
⛳ Common Use Cases for Cloudflare Firewall Rules
Cloudflare firewall rules are versatile tools that can be used to address a variety of security and traffic management needs. In this section, we will look at several common use cases for these rules and how they can enhance the security and functionality of your web application.
🔆 DDoS Protection
Distributed Denial of Service (DDoS) attacks are a prevalent threat to web applications, overwhelming servers with a flood of traffic. Firewall rules can help mitigate these attacks in a couple of ways. First, you can block known attack sources by using firewall rules to block IP addresses or networks that are known to participate in DDoS attacks. Additionally, you can implement rate-limiting rules to restrict the number of requests from individual IP addresses or networks, limiting the impact of DDoS attacks.
🔆 Preventing SQL Injection
SQL injection is a common web application attack where malicious SQL statements are inserted into an entry field for execution. Firewall rules can help prevent this by blocking requests containing common SQL injection patterns, such as SELECT and UNION keywords combined with specific characters. Moreover, you can use Cloudflare’s managed rulesets to block known SQL injection techniques automatically.

🔆 Blocking IPs or Countries
Sometimes, you may want to restrict access to your web application based on IP addresses or geographic regions. Cloudflare makes this straightforward. You can create rules to block traffic from specific IP addresses or ranges that are known to be malicious or unwanted. Additionally, you can use firewall rules to block or allow traffic from specific countries based on your business needs or security concerns.
🔆 Custom Access Control
Cloudflare firewall rules offer the flexibility to implement custom access control based on various criteria. For instance, you can create rules that restrict access to specific URLs or URL patterns based on criteria such as IP address, user agent, or HTTP method. You can also use firewall rules to restrict access to sensitive areas of your website, such as administrative pages, by IP address or other identifying characteristics.
🔆 Protecting APIs
APIs are often targeted by malicious actors seeking to exploit vulnerabilities or overload the system. Firewall rules can help protect your APIs by restricting access based on IP address, API key, or other identifying factors. Additionally, you can implement rate-limiting rules to prevent abuse of your APIs and ensure fair usage.
🔆 Enforcing User Agent Policies
User agents identify the client making a request, and firewall rules can be used to enforce policies based on this information. You can create rules to block requests from known malicious or suspicious user agents or allow only specific user agents if your web application is intended for specific clients.
These rules provide versatile solutions for a wide range of use cases, including DDoS protection, preventing SQL injection, blocking specific IPs or countries, custom access control, protecting APIs, and enforcing user agent policies. By leveraging these use cases, you can enhance the security and functionality of your web application.
⛳ Troubleshooting Firewall Rules and Tips to Manage
Despite the best planning and implementation, issues may arise when using firewall rules. Here, we will explore common problems and provide debugging tips so that you already know how to resolve the issues if they arise.
💠 Common Issues
There are many problems that could arise, which is making problems. From many, these are the common troubleshooting issues we are discussing below:
- Legitimate Traffic Blocked: One common issue is when legitimate traffic gets blocked unintentionally. This often happens when rules are too broad or too strict.
- Unexpected Behavior: Sometimes, firewall rules might not behave as expected, often due to rule precedence issues or overlapping conditions.
- Performance Impact: While rare, firewall rules can sometimes impact site performance if they are misconfigured or overly complex.
💠 Debugging Tips
Check out these debugging tips so that you can ensure the firewall rules you have created run smoothly without making problems further:
- Use the Firewall Analytics: Cloudflare provides detailed analytics for its firewall, showing which rules are triggered and how often. Use this to identify problem rules.
- Review Rule Order: Cloudflare evaluates firewall rules in order of priority. Review the order of your rules to ensure that higher-priority rules do not unintentionally override lower-priority ones.
- Test with Preview Mode: Before fully enabling a rule, use Cloudflare’s preview mode to test how it will behave with incoming traffic. This helps catch issues before they impact real users.
- Adjust Rule Conditions: If a rule is blocking legitimate traffic, consider refining the conditions to be more specific. For example, instead of blocking all traffic from a country, you might block specific IP ranges or use rate limiting.
- Check Rule Actions: Make sure the actions for your rules are appropriate. For example, if you are testing a new rule, you might want to log traffic rather than block it outright.
🥷 Setup Cloudflare Firewall Rules & Secure Your Web App
Cloudflare firewall rules are a vital tool for any website owner looking to enhance the security of their web application. With their flexibility, customisation options, and powerful analytics, these rules provide a robust defense against a wide range of threats. By following best practices and troubleshooting issues effectively, you can leverage Cloudflare firewall rules to keep your web application secure and running smoothly.
If you find this blog helpful and want to read more blogs like this one, Subscribe to our blogs and Join our Facebook Community to connect with more people with common interests.