These days, many web applications let you export data into CSV files. While this is super handy, it can also lead to a risk known as CSV injection. It is important to make sure these exported files are safe and do not leave users vulnerable to attacks. In this blog post, we will take a closer look at CSV injection and how you can prevent it to protect your data.

What is CSV Injection & When It Occurs?
CSV Excel Macro Injection, also known as Formula Injection or CSV Injection, is an attack method used in regular penetration testing of applications. CSV injection is a vulnerability found in applications that allow users to export data as spreadsheets. These spreadsheets are generated from user inputs that have not been properly validated or filtered.
Many modern web applications let users download data in .csv or .xls file formats. This is convenient for spreadsheet applications like MS Excel and OpenOffice Calc, but it also means that cells in the spreadsheets can include data from untrusted sources. Consequently, users who open these exported spreadsheets may be at risk.
CSV Injection Attack: In Simple Terms
✅ A CSV Injection Attack happens when malicious websites insert harmful code into CSV files.
✅ This attack is particularly dangerous because it exploits cells starting with these characters: equal sign (=), plus sign (+), minus sign (-), and the @ symbol.
✅ When the harmful code is entered as a formula in a CSV file, it can execute commands that harm the computer by manipulating, accessing, or deleting user data.
✅ Another method for this attack is through DDE (Dynamic Data Exchange), which allows the execution of arbitrary code on the computer.
How Does CSV/Formula Injection Attack Work?
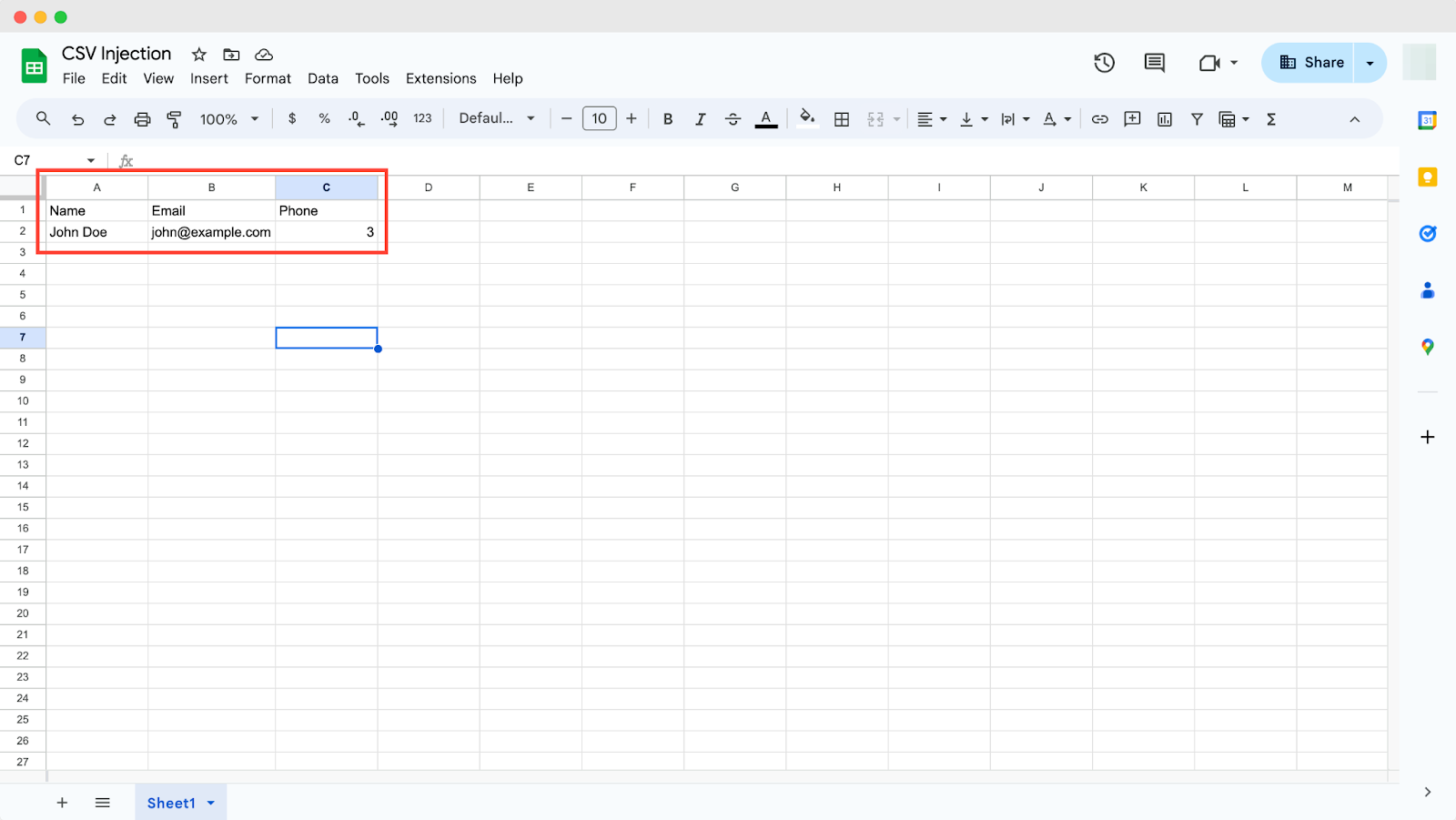
To learn how the CSV injection attack works, let us have a look at the below data set. The first row lists the column headers of the data set: Name, Email, and Phone.
Each following row contains a contact’s data, with values separated by commas. This data includes each person’s name, email address, and phone number.
John Doe,john@example.com,=SUM(1,2)
Jane Smith,jane@example.com,555–1234
In this example, an attacker could inject a formula like =SUM(1,2) into the third column. When the CSV file is opened in a spreadsheet application, it would perform unintended calculations.
Here is how it might happen in a real-world application:
Suppose you have an app that collects user input. When the user clicks the ‘Submit’ button, the app sends the data to the backend and generates a CSV file. If the backend does not validate the input, it is vulnerable to this kind of attack.
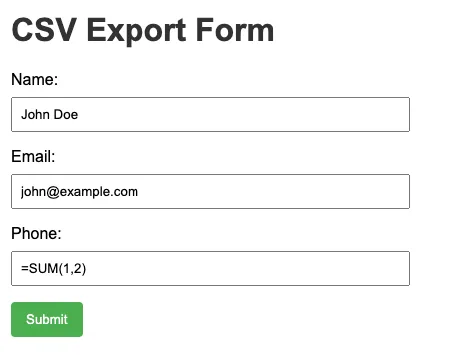
Since there is no validation, any field can be targeted. The attacker chose the Phone field and injected the formula =SUM(1,2).
When the user opens the downloaded file in Excel/Google Sheets, the Phone field will display the number 3 because the formula adds 1 and 2.
You might think it is no big deal. After all, someone just added up two numbers; it can not harm you or your customers. But in reality, it actually does.
For example, hackers can sneak into a user’s computer using something called a reverse shell. The formula makes the computer download a harmful exploit.exe file from the web and run it. This gives the hacker access to the user’s system.
Sometimes, hackers trick users into clicking links that take them to malicious websites. They can even steal Google Docs. You can see how risky this is! And there are many more ways hackers can cause trouble. So, you need to know how to prevent this CSV injection to protect your data.
CSV Injection Prevention: The Easiest and Possible Solutions
CSV injection can be a real threat if user input is not handled properly before adding it to a CSV file. Here is a straightforward guide to keep your CSV files safe:
General Tips to Prevent CSV Injection
💡 Avoid Direct User Input: If possible, do not use user input directly in your CSV files.
💡 Validate Input: Check that the input meets the expected criteria.
💡 Sanitize Input: Clean the input to remove any harmful content.
Important Characters to Watch Out For
There are a few things you need to be aware of while preventing CSV injection. Keep an eye on these characters:
👉 Equals sign (=)
👉 Plus sign (+)
👉 Minus sign (-)
👉 At symbol (@)
👉 Tab (0x09)
👉 Carriage return (0x0D)
Handling Dangerous Characters
It is not enough to ensure that user input does not start with these characters. Be cautious of field separators (like commas or semicolons) and quotes, as these can help attackers manipulate the cell content.
Safe Practices
To ensure safety, apply these methods to each CSV field:
💡 Wrap Fields in Double Quotes: This helps the spreadsheet editor read the content as text.
💡 Prepend with a Single Quote: This further ensures that the content is treated as text.
💡 Escape Double Quotes: Use an additional double quote to escape each double quote in the content.
By following these simple steps, you can significantly reduce the risk of CSV injection and keep your data secure.
Let us have a few examples 👇
| Before Sanitization | After Sanitization |
| =1+2″ ; = 1+2 | ” ‘=1+2″” ; = 1+2″ |
| =1+2′ ” ; ,= 1+2 | ” ‘=1+2’ “” ; ,= 1+2″ |
Sanitize Files and Prevent CSV Injection Easily
CSV injection is a significant security risk for web applications that allow data export to CSV files. This type of attack can lead to data manipulation, unauthorized access, or even the execution of harmful commands. To protect against CSV injection, it is crucial to sanitize CSV files before they are opened.
If you have found this blog helpful, feel free to subscribe to our blogs for valuable tutorials, guides, knowledge, and tips on web hosting and server management. You can also join our Facebook community to share insights and engage in discussions.